The ScarCruft Korean-speaking APT is changing up its espionage tactics to include an unusual piece of malware devoted to harvesting Bluetooth information – while also showing some overlap with the DarkHotel APT.
An analysis of ScarCruft’s binary infection procedure by Kaspersky Lab shows that in a campaign that continued over the course of 2018, the group used a multi-stage process to update each of its malware modules effectively while also evading detection.
The researchers said that spear-phishing and the use of various public exploits remain ScarCruft’s go-to initial attack vectors. Once the victim is compromised, the attack installs an initial dropper, which uses a known exploit for CVE-2018-8120 to bypass Windows User Account Control (UAC) in order to execute the next payload, a downloader, with higher privileges. This stage connects with the command-and-control (C2) server to grab the next payload, which is hidden in an image using steganography.
“The downloaded payload is an image file, but it contains an appended malicious payload to be decrypted,” Kaspersky Lab researchers said, in a posting on Monday.
That payload is a full-featured backdoor and information exfiltration remote access trojan (RAT) known as ROKRAT. The malware can download additional payloads, execute Windows commands, save screenshots and audio recordings, and exfiltrate files.
“Upon execution, this malware creates 10 random directory paths and uses them for a specially designated purpose,” the researchers explained. “The malware creates 11 threads simultaneously: six threads are responsible for stealing information from the infected host, and five threads are for forwarding collected data to four cloud services (Box, Dropbox, Pcloud and Yandex).”
While ROKRAT is a known baddie, Kaspersky Lab researchers were also able to confirm that ScarCruft is expanding its exfiltration targets to mobile devices. The APT is using a unique, custom Bluetooth device harvester, which collects information directly from the infected host, including device name, device class, whether it’s connected to anything else, address, authentication state and whether it’s trusted/remembered.
DarkHotel Overlaps
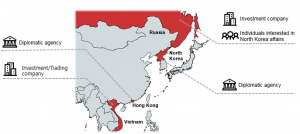
In the analyzed campaign, which started last spring, ScarCruft appears to have taken aim at investment and trading companies in Vietnam and Russia, plus a diplomatic agency in Hong Kong and another in North Korea. Typically, the APT goes after organizations and companies with links to the Korean peninsula, according to researchers.
“We believe [the victims] may have some links to North Korea, which may explain why ScarCruft decided to closely monitor them,” the researchers said. “We discovered one victim from Russia that also triggered a malware detection while staying in North Korea in the past. The fact that this victim visits North Korea makes its special and suggests that it may have valuable information about North Korean affairs.”
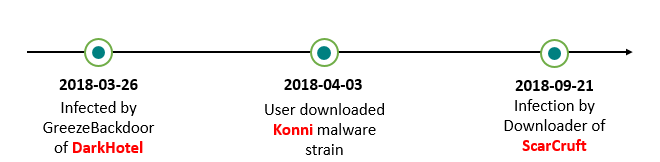
Interestingly, while ScarCruft infected this victim on September 21, the DarkHotel APT also targeted this victim, back in March 2018.
Darkhotel was first identified in 2014 by Kaspersky Lab researchers, who said the group had been active since at least 2007. The group was known for targeting diplomats and corporate executives via Wi-Fi networks at luxury hotels – and has since then continued accessing zero-day vulnerabilities and exploits.
In the DarkHotel attack, the victim was infected with the GreezeBackdoor, a known custom tool of the DarkHotel APT group; and then in April, it was infected by another DarkHotel tool, the Konni malware, which was disguised as a North Korean news item in a weaponized document.
“This is not the first time we have seen an overlap of ScarCruft and DarkHotel actors,” Kaspersky Lab researchers said. “They are both Korean-speaking threat actors and sometimes their victimology overlaps. But both groups seem to have different tactics, techniques and procedures, and it leads us to believe that one group regularly lurks in the other’s shadow.”
The researchers concluded that the ongoing evolution of ScarCruft’s malware approach as well as its interest in attacking those in the business sector who may have any connection to North Korea will likely contribute to additional attacks going forward.
“The threat actor is highly skilled and, by all appearances, quite resourceful,” the researchers said. “The actor is still very active and constantly trying to elaborate its attack tools…[and] the attackers appear to be increasing the scope of the information collected from victims.”
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.