Silent Librarian is targeting university students in full force with a revamped phishing campaign. The threat group, aiming to steal student login credentials, is using new tricks that bring more credibility to its phishing emails and helping it avoid detection.
The threat group (also known as TA407 and Cobalt Dickens), which operates out of Iran, has been on the prowl for credentials since the start of the 2019 school year in September, launching low-volume, highly-targeted, socially engineered emails that eventually trick students into handing over their login credentials.
But more recent campaigns show the cyberattackers using shortened URL links in their phishing emails, which make it more difficult to detect that victims are being redirected to an attacker-hosted landing page. The attackers have also revamped their landing pages with new university-specific banners, based on weather alerts or emergency notifications, to make them look more authentic.
“The changes in URL shorteners, linking and hosting practices described here make detection of TA407’s activities increasingly difficult for defenders and demonstrate the adaptability and innovation that have enabled this threat actor to drive billions of dollars in losses in terms of intellectual property theft and resale of stolen journal subscriptions,” said Proofpoint researchers, in an analysis this week.
Back-To-School Attacks
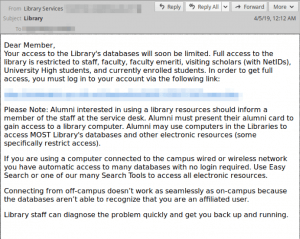
The attacks start with phishing messages to students with themed subject lines (such as “renewal of loaned items” or “library services”) purporting to come from the school administration or library. These messages contain links to spoofed login pages for resources associated with the targeted universities. Recipients who click the links are directed to a web page that looks identical or similar to the spoofed library resource.
After the victims enter their credentials, their web browsers are redirected to the next.php file, where the credentials are stored locally in the pass.txt file. The victim’s browser is then sent to the legitimate site being spoofed.
This attack method has been highly successful for Silent Librarian: In fact, in September researchers said that at least 20 new phishing domains were targeting more than 60 universities in Australia, Canada, Hong Kong, Switzerland, the United Kingdom and the United States have cropped up.
More recently, researchers said that they observed campaigns ramping up over the past few weeks, with new Freenom domains appearing to host phishing pages (a full list of the more recent domains can be found here).
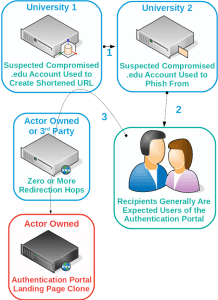
“Historically, the group has employed the use of a series of phishing origin points, abusing access first at one university and then another,” they said. “TA407 makes extensive use of Freenom domains to host credential phishing landing pages; the group then abuses compromised accounts at universities to phish users at other universities, compromising additional accounts and spreading from school to school.”
New Tricks
In a new technique not previously observed, researchers said that Silent Librarian cyberattackers have updated how they utilize URLs in their phishing emails to trick victims into clicking on the links.
Historically, the cyberattackers used shortening URL services (for initial redirection to phishing landing pages) such as the (now-discontinued) Google URL shortening service and .ir-based short URL services.
However, researchers say they have more recently observed “apparent experimentation” with university-based URL shorteners from universities that they have previously compromised. Researchers believe this is due to the discontinuation of Google’s goo.gl services.
Many organizations, especially universities, stand up their own URL shortening services to allow students and staff to share content (such as a long link in an academic journal or a paper hosted on a deep directory structure) easily without relying on third-party services like bit.ly, researchers told Threatpost.
Because of the nature of these services, the URL gives no clue as to the actual content of the link. That said, a link like [goo.gl/abc123] is more likely to set of red flags than one that comes from a school’s domain or known short URL service (i.e one that looks like this: [<the school’s domain>.edu/abc123]), Chris Dawson, threat intelligence lead at Proofpoint, told Threatpost.
“These services help to make fraudulent links appear legitimate to targeted users and mask their true destination, increasing the likelihood of a successful breach,” Dawson told Threatpost. “TA407’s use of shortened URLs demonstrates the adaptability that has enabled them to drive billions of dollars in losses in terms of intellectual property theft and resale of stolen journal subscriptions.”
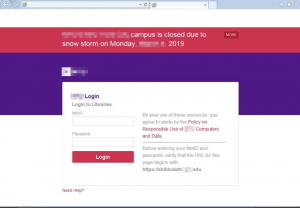
In another trick used in more recent campaigns, researchers said that Silent Librarian is also taking advantage of publicized downtime or weather alerts, among other events, to add credibility to the phishing landing page.
For example, in one spoofed landing page researchers observed weather notification banners that mimic a notification being used in the real login portal: “The awareness manifests in both the lure wording and/or landing page appearance,” researchers said. “However, Proofpoint researchers do occasionally observe what appears to be an outdated clone of a previous version of their target’s portal, suggesting either inconsistent updates or coincidental timing of clone updates.”
Looking ahead, researchers recommend that universities remain vigilant against these threats to prevent losses and protect valuable IP and personal information.
“Implementing two-factor authentication within publicly exposed systems can help mitigate overall attack risk and substantially increase the level of effort needed by threat actors to compromise university accounts,” said researchers.
What are the top cybersecurity issues associated with privileged account access and credential governance? Experts from Thycotic on Oct. 23 will discuss during our upcoming free Threatpost webinar, “Hackers and Security Pros: Where They Agree & Disagree When It Comes to Your Privileged Access Security.” Click here to register.