In a sudden about-face, Sun has rushed out a Java update to fix a drive-by download vulnerability that exposed Windows users to in-the-wild malware attacks.
In a sudden about-face, Sun has rushed out a Java update to fix a drive-by download vulnerability that exposed Windows users to in-the-wild malware attacks.
The patch comes less than a week after Sun told a Google researcher it did not consider the issue serious enough to warrant an out-of-cycle patch and less than a day after researchers spotted live exploits on a booby-trapped song lyrics Web site.
The release notes that accompanies the new Java 6 Update 20 makes no mention of the public flaw disclosure or subsequent attacks but I’ve been able to confirm that the patch does cover the vulnerability released by Google security researcher Tavis Ormandy.
After applying the fix on a Windows machine, Ormandy’s proof-of-concept demo did not work. Instead of opening the calculator application, I got an error message concerning the Java Virtual Machine Launcher:
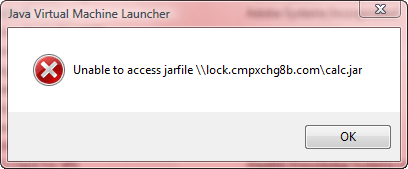
The flaw, which was also discovered independently by Ruben Santamarta, occurs because the Java-Plugin Browser is running “javaws.exe” without validating command-line parameters.
Despite the absence of documentation, a researcher was about to figure out that Sun removed the code to run javaws.exe from the Java plugin.
Here is a link to download the Java 6 Update 20 fix.
The about-face by Sun is another sign that some big vendors still struggle to understand the importance of working closely with white hat researchers to understand the implications of certain vulnerabilities. In this case, Google’s Ormandy was forced to use the full-disclosure weapon to force the vendor into a proper response.
It’s incomprehensible that a software vendor like Sun, now under Oracle’s wings, could have misdiagnosed this vulnerability when Ormandy originally reported it. It was clear, from the inception, that this was a “critical” issue that was found by several different hackers. On Twitter, Ormandy said he had no information that the issue was already in the wild before he wielded the full-disclosure stick. However, he maintains “it was just too trivial for that not to be the case.”
To this date, Oracle Sun has not publicly commented or mentioned the public disclosure of an issue that’s being actively exploited.
Speaking of irresponsible, here’s what I saw when during the process of applying Java patch this morning. Yes, checked by default. Sigh.