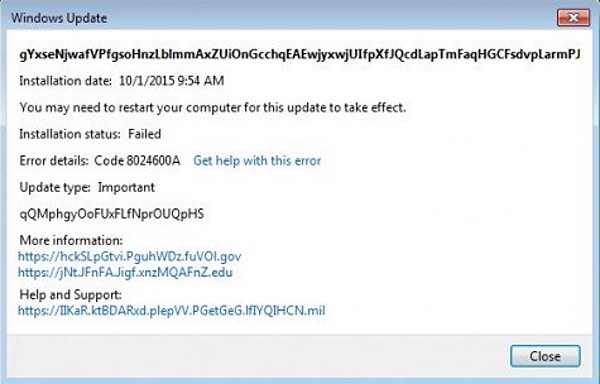
A suspicious Windows 7 update today raised concern on a number of Microsoft and technology forums that the Windows Update service had been compromised. Microsoft, however, cleared the air several hours later admitting that the update was their mistake.
“We incorrectly published a test update and are in the process of removing it,” said a Microsoft spokesperson
A compromise of such an automated update service would have had devastating results. Automated software update services have long been speculated as a means to spread malware at scale. Attackers or governments that infiltrate something like Windows Update could compromise software updates to the point where such services are no longer trusted, leaving endpoints and servers unpatched and at greater risk.
Rated important, the mysterious update, purportedly a new language pack, showed up early this morning on home and business users’ machines. The update was 4.3 MB in size and included long, random character file names and redirects to different .mil, .gov and .edu domains—both of which were out of the norm for Windows updates.
The update has since disappeared from Windows Update, but not before it was pushed mostly to consumers via Windows Update. Some users said the update to install on their machines. Others who successfully installed the update essentially bricked their machines, according to replies on the original Windows 7 forum post.
Windows Update and Windows Server Update Services (WSUS) are especially juicy targets. At Black Hat this summer, researchers Paul Stone and Alex Chapman of Context Information Security of the U.K. demonstrated weaknesses in WSUS that are difficult to address and expose any server or desktop using its automated updates to compromise.
Just last week, the Washington Post reported that the U.S. government explored several approaches that technology providers could implement to cure the Going Dark crypto issue. Law enforcement and government officials have expressed concern over recent changes from Apple and Google, in particular, to divorce themselves from storing encryption keys. The practice, government says, hinders law enforcement and national security investigations. They suggest, according to the Post article, that under a court order, the government could drop spyware on machines via software update services.
At TrustyCon, a 2014 event adjunct to RSA Conference, ACLU principal technologist Chris Soghoian delivered a talk that also suggested the next wave of surveillance efforts could target update services.
Soghoian said his concern is that the government will not only exploit the convenience of these update services offered by most large providers, but also that it will erode the trust users have in the services leaving them vulnerable to cybercrime, identity theft and fraud.
“There are really sound security reasons why we want automatic security updates. If consumers have to do work to get updates, they won’t, and they will stay vulnerable,” Soghoian said in 2014. “What that means though is giving companies root on our computers—and we really don’t know what’s in the code after fact. This is a point of leverage the government can use. We have no evidence they are using it right now, but these companies have a position of power over our devices that is unparalleled.”