More threat actors are pushing weaponized Excel web query (IQY) files to deliver malicious code – as seen in recent campaigns by several major malspam distributors.
Researchers at IBM X-Force this week disclosed that both the Necurs Botnet, as well as DarkHydrus and the threat actor behind the Marap downloader, have all been observed utilizing weaponized IQY file attachments to deliver malware.
Microsoft Excel uses a URL embedded into an IQY file attachment to pull data from the internet into a spreadsheet (albeit after a security prompt for the user built into the file). Because IQY files are inconspicuous, it makes them an attractive target for threat actors to insert malicious URLs into them, which are then executed when a victim opens it, researchers said.
“This type of file attachment is relatively unusual and not commonly seen attached to emails, and that is why it can be interesting to an attacker,” Scott O’Neill, security researcher with X-Force, said this week in a post. “Attackers constantly shuffle file types in their spam campaigns in an attempt to create an element of surprise for unsuspecting users.”
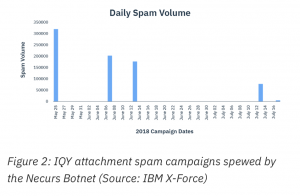
The prolific Necurs botnet, which has used IQY attachments in previous campaigns, has been most recently seen using the attachments to deliver the FlawedAmmyy trojan between late May and mid-July 2018. X-Force researchers said they caught over 780,000 spam emails containing the tricky attachments from the Necurs resources in their spam traps.
This shows evidence that this was a mass phishing attempt targeting anyone willing to open the attachments and enable a data connection to allow the embedded URL to do its job, O’Neill told Threatpost.
“After a user clicks on the malicious IQY attachment and enables the data connection, the infection chain begins,” O’Neill told Threatpost. “The user’s device connects to the embedded URL and fetches a PowerShell script which eventually downloads and installs the FlawedAmmyy RAT.”
The emails looked to be of the typical format seen from the Necurs Botnet, O’Neill told us – they contained a single attachment and the body of the emails were empty.
“They also used a commonly seen subject theme ‘unpaid invoice [ID:<random number>]’ that has been used by Necurs and other spam senders,” he said. “Another red flag that should stand out is the fact that these emails are coming from unknown addresses.”
 He added, “Users might see IQY attachments from other co-workers since they are commonly seen in networks that utilize SharePoint.”
He added, “Users might see IQY attachments from other co-workers since they are commonly seen in networks that utilize SharePoint.”
DarkHydrus is another threat actor that researchers have seen using the malicious attachments. It uses spear-phishing emails that contain Roshal Archive Compressed (RAR) files, which conceal a weaponized IQY file, the X-Force team said. Most recently, in August the group was seen targeting government entities and educational institutions in the Middle East in a credential-harvesting campaign.
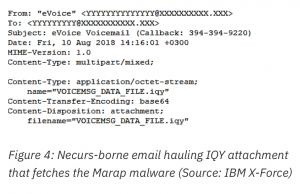
Finally, the Marap downloader presented the most recently observed use of malicious IQY attachments in a campaign that started in Aug. 10, O’Neill said. The malware was discovered as part of a new campaign primarily targeting financial institutions.
Looking forward, O’Neill told Threatpost he expects the trend of malicious actors peddling malware through IQY attachments to increase. The best prevention tactic is ensuring employees are educated about IQY files as part of phishing training, as well as developing group policies to block IQY files.
“This tactic is still fairly new, I expect we will see malicious IQY attachments used in other campaigns,” he told us. “Since writing my recent blog post on malicious IQY attachment activity, other researchers found another spam campaign targeting banks with IQY attachments embedded into PDFs. I think we will see this type of activity for some time.”