The high-velocity application- and process-development practices collectively known as DevOps has become a core goal for many enterprises, as they look to respond to market forces more dynamically. This embrace is pushing container deployments forward as necessary tools for executing the vision of flexible resource allocation. However, as ever, security seems to be lagging behind.
In fact, 60 percent of respondents in a recent survey admitted that their organizations had been hit with at least one container security incident within the past year. In companies with more than 100 containers in place, that percentage rises to 75 percent.
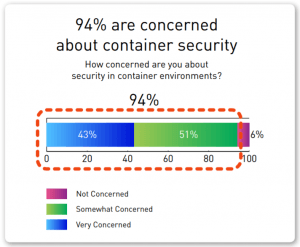
That’s according to Tripwire’s State of Container Security Report released Monday, which surveyed 311 IT security professionals at companies with over 100 employees. It also found that a full 94 percent of respondents said they have container security concerns, with 71 percent predicting that container security incidents would increase in the new year.
“Organizations will confront growing complexity and risk as they work to scale their DevOps initiatives in 2019,” according to the report. “Part of this risk will come from their containers, for many organizations still lack transparency into these software pieces. If they are to adequately mitigate their risk and minimize their exposure to digital threats, organizations will need to secure their containers.”
Containers (i.e., Kubernetes, Mesos, Docker Swarms and more) are essentially lightweight application packages that share a single operating system kernel with other containers on a cloud server. They support DevOps because they use far fewer resources than virtual machines and are therefore more responsive. They also can be instantiated in an on-demand way, so they can be spun up almost instantly when needed and can disappear when they are no longer required – further freeing up host resources and engendering significant flexibility for businesses.
However, despite the benefits, it means there are more moving parts to consider from a security perspective.
As a result, just 12 percent of respondents to Tripwire’s survey said they could detect a compromised container within minutes. Forty-five percent of survey participants said it would take hours, while some estimated it would take even longer.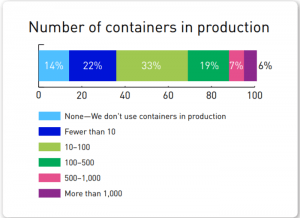
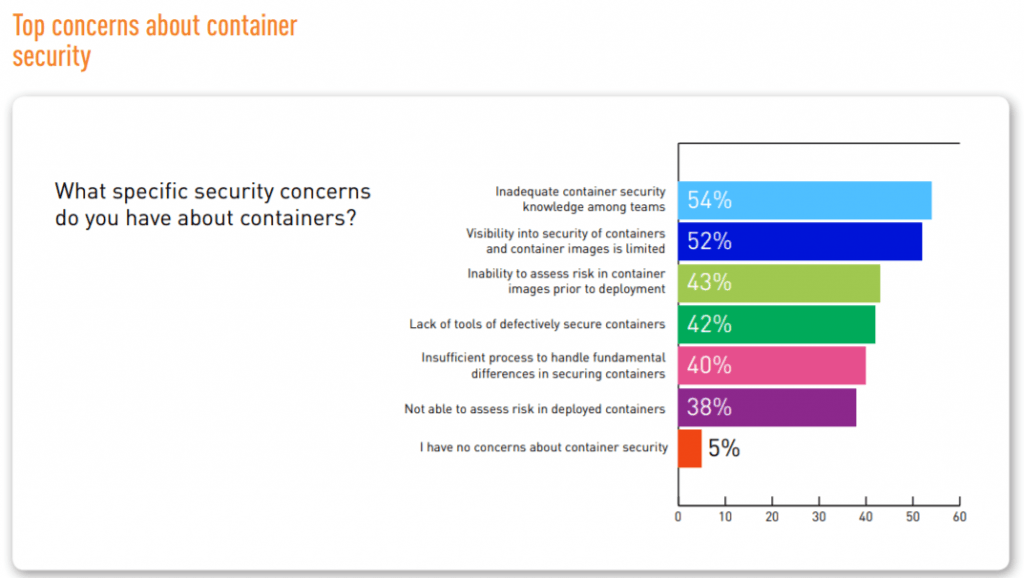
At the same time, nearly half (47 percent) of IT security professionals said their organizations have vulnerable containers in production, while nearly the same number (46 percent) said they were unsure if this was the case.
“With the increased growth and adoption of containers, organizations are feeling the pressure to speed their deployment,” said Tim Erlin, vice president of product management and strategy at Tripwire. “To keep up with the demand, teams are accepting risks by not securing containers. Based on what this study found, we can see that the result is a majority of organizations experiencing container security incidents.”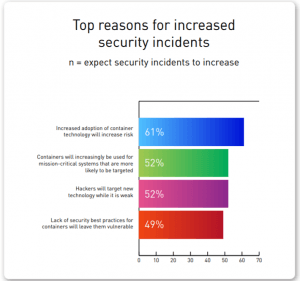
Interestingly, despite overall DevOps enthusiasm, 42 percent of respondents to Tripwire’s survey said their organizations are limiting their container adoption because of the attendant security risks. Almost everyone said they wanted additional security environments (98 percent), and 82 percent are thinking about restructuring security responsibilities because of container adoption.
Containers have slowly emerged as a new cyber-battleground: Researchers in June found over a dozen malicious docker images available on Docker Hub that allowed hackers to earn $90,000 in cryptojacking profits. Shortly after that, it was revealed that more than 22,000 container orchestration and API management systems were unprotected or publicly available on the internet as of June.
According to research from Lacework, containers tend to suffer from poorly configured resources, lack of credentials and the use of non-secure protocols. As a result, attackers can remotely access the infrastructure to install, remove or encrypt any application that the company is running in the cloud.