A study of abandoned websites owned by leading global corporations hammers home the point that old web applications need to be properly mitigated or retired. Otherwise, these resources often haunt a firm long after they have been forgotten.
Researchers at High-Tech Bridge used the Financial Times 500 list of leading companies and unearthed a number of concerns when it comes to forgotten web applications.
 “Abandoned, shadow and legacy applications undermine cybersecurity and compliance of the largest global companies, despite growing security spending,” according to the aptly named research report, “Abandoned Web Applications: Achilles’ Heel of FT 500 Companies.”
“Abandoned, shadow and legacy applications undermine cybersecurity and compliance of the largest global companies, despite growing security spending,” according to the aptly named research report, “Abandoned Web Applications: Achilles’ Heel of FT 500 Companies.”
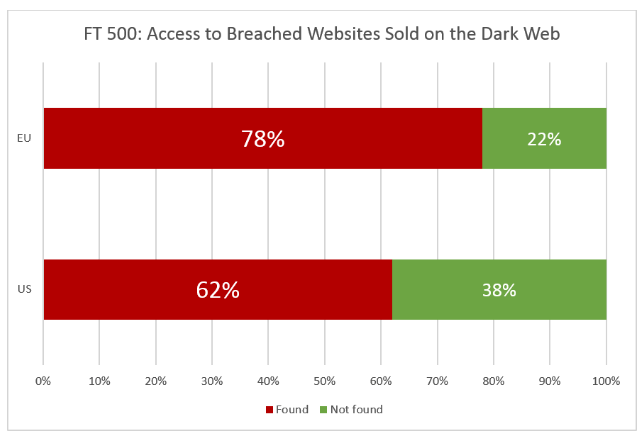
According to the report, 70 percent of FT Global 500 firms have access to a portion of their websites being sold on the internet black market. An additional 92 percent of external web applications have exploitable security flaws or weaknesses.
“A U.S. company has an average of 85.1 applications that can be easily discovered externally and are not protected by 2FA [two-factor authentication], strong authentication or other security controls aimed to reduce application accessibility to untrusted parties,” according to the report.
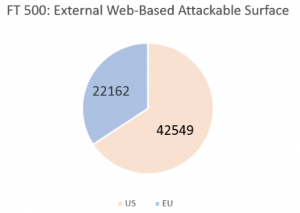
For its study, High-Tech Bridge said it created a list of 1,000 firms culled from both FT US 500 and the FT Europe 500. Next, it assessed the vulnerability of both external web and mobile applications, SSL certificates, web software and cloud storage.
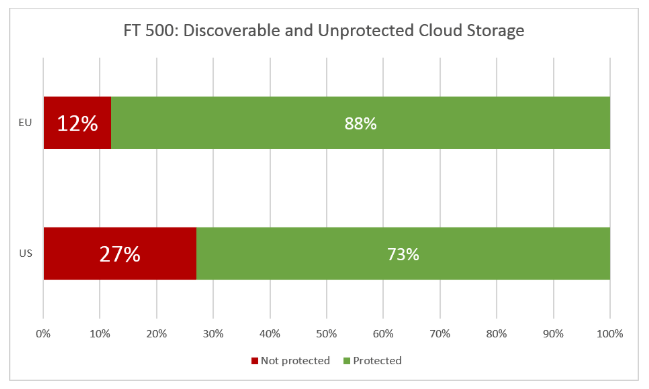
It discovered that worldwide, 19 percent of the companies examined have external unprotected cloud storage, and that only 2 percent of external web applications are properly protected with a web application firewall.
It’s worse stateside. “Twenty-seven percent of the U.S. companies have at least one external cloud storage (e.g. AWS S3 bucket) accessible without any authentication from the internet. Only 12 percent of the European companies have the same issue,” the study found.
Misconfigured storage servers leaking data to the internet have plagued companies recently. Insecure cloud storage has consistently made headlines impacting personal and sensitive data under the control of U.S. military contractors, Verizon partners, Walmart merchants and marketing firms.
Researchers also found that less than 20 percent of discovered web servers in both the U.S. and E.U. have an SSL/TLS configuration compliant with the most recent version of the payment-card security standard, PCI DSS 3.2.1.
The report noted, “48.81 percent of web servers belonging to the U.S. companies have an ‘A’ grade for their SSL/TLS encryption, while 32.21 percent have a failing ‘F’ grade. 7.82 percent still have vulnerable and deprecated SSLv3 protocol enabled.”
When it comes to WordPress, which is now the back-end platform for 32 percent of all websites, things also look bleak. According to the report, “among the web applications of the U.S. companies that run WordPress, 94 percent have a default admin location (on /wp-admin URL) not protected by any additional means (e.g. supplementary .htaccess authentication or IP whitelisting).”
Things were worse in Europe, with 99.5 percent of WordPress sites suffering from the same weak admin location. “Default WordPress admin area location simplifies bruteforcing and other authentication-related attacks, including password re-use in case of admin account compromise on a third-party resource, and exploitation of XSS vulnerabilities in WP plugins and themes,” the report stated.