When it comes to distributed denial of service (DDoS) attacks, the third quarter of 2018 marked an apparent lull in the action, with fewer huge, multi-day attacks than in previous quarters. Researchers however warn against having a false sense of security: The total number of attacks in the quarter stayed steady.
Breaking that down a bit, an analysis by Kaspersky Lab showed that short attacks with a duration of under four hours grew 17.5 percentage points, to account for 86.94 percent of attacks.
That was balanced out by the fact that the number of sustained attacks declined in the quarter.
“[The decline] is true not only for the ‘champions,’ which lasted upward of 140 hours, but also for all the other categories down to five hours,” according to the report. “The most dramatic decline occurred in the five to nine hours of duration category: These attacks were down to 5.49 percent from 14.01 percent.”
When they did appear, they were notable. The longest attack in Q3 lasted 239 hours – just short of 10 days.
Distribution by type of attack was almost the same as the previous quarter. The SYN flood method kept its first position; its share grew even more to 83.2 percent (from 80.2 percent in the second quarter and 57.3 percent in Q1). UDP traffic came in second; it also edged upward to settle at 11.9 percent (last quarter the figure was 10.6 percent).
Other types of attacks lost a few percentage points but suffered no change in terms of relative incidence: HTTP is still third, while TCP and ICMP – fourth and fifth respectively.
The analysis also showed that there were variations by month and type of attack.
Compared to Q3 of last year, the number of DDoS attacks slightly increased due to a rash of new attacks in September. However, the rest of the summer was marked with a noticeable drop in the number of DDoS attacks. The spike in September represented about five times more attacks compared to September 2017.
“The DDoS upsurge exactly in September is a fairly common thing: The primary target, year after year, is the education system, attacks being directed at the web resources of schools, universities and testing centers,” according to Kaspersky Lab. “The attack on one of England’s leading schools, Edinburgh University, which began on September 12 and lasted for nearly 24 hours, made the biggest headlines this year.”
Meanwhile, DDoS attacks coming from botnets peaked in August; and Kaspersky Lab said that the share of Linux botnets has grown only slightly from the last quarter. In this context, the by-type distribution of DDoS attacks has not changed much: SYN flood still comes first (83.2 percent).
The day of week distribution was fairly even this quarter. Saturday now is the most “dangerous” day of the week (15.58 percent), having taken over from Tuesday (13.70 percent). Tuesday is now second-to-last in terms of the number of attacks, just ahead of Wednesday, currently the quietest day of the week (12.23 percent)
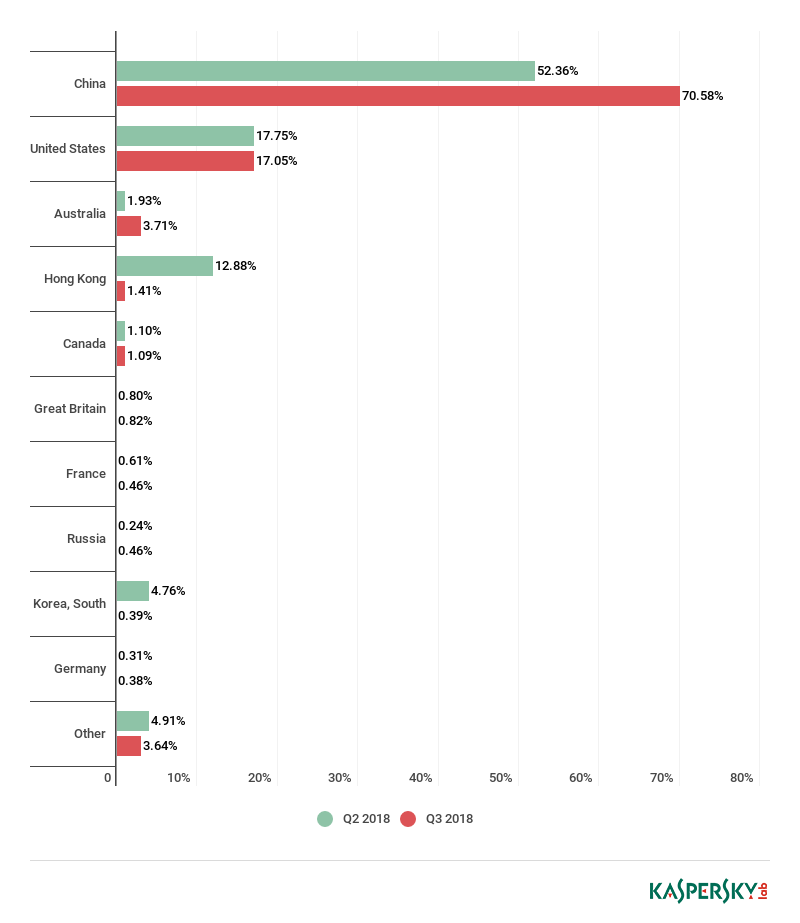
On the geography front, in line with previous quarters, China topped the list for the highest number of attacks (78 percent). However, the U.S. has reclaimed its second position (12.57 percent), while Australia came in third (2.27 percent) – higher than ever before. For the first time, South Korea departed the top 10 list.
“[South Korea’s] share shrank from 3.21 percent last quarter to 0.30 percent for a downhill ride from fourth to eleventh position,” the report found. The stats also showed that the combined percentage of all the countries from outside the top 10 has dropped from 3.56 percent to 2.83 percent.
Attacks by Country:
The number of unique targets meanwhile increased by 63 percent, worldwide.
Fewer DDoS Headlines for Q3
There were only three “major” attacks in the quarter, according to Kaspersky Lab analysis: There was an early July attack on Blizzard Entertainment, a late-July offensive directed at game publisher Ubisoft, and a days-long onslaught against three online poker sites (America’s Card Room, PokerStars and Partypoker), in August.
Blizzard’s Battle.net servers were offline for almost three days, preventing online gaming for the duration. A group called PoodleCorp took responsibility. In the Ubisoft instance, players were having trouble logging on to their accounts and using the multiplayer mode; and in the poker campaign, events were canceled, leading to big losses for players.
The quarter also saw politically motivated DDoS attacks, researchers noted. These included an attack on governmental service DigiD in Netherlands at the end of July that blocked taxation-related features for citizens, a six-minute long disruption of the Swedish Social Democratic Party’s website at the end of August, and a campaign against the Ministry of Labor of the Republic of South Africa.
Small Additions to the Toolsets
The botnets responsible for most DDoS attacks remained in play over the third quarter, including new versions of Mirai and Gafgyt botnets seen exploiting known vulnerabilities in SonicWall and Apache Struts in late August and early September.
There were two notable toolset occurrences in the quarter. For one, researchers detected a mass device recruiting campaign targeting D-Link routers in July, which used over 3,000 IPs and just one command server.
“The exploit was not very successful in corporate environments; yet it is still to be seen whether it was able to create a new botnet of user routers (and how big at that),” Kaspersky Lab said.
July also saw the emergence of Trojan Death, which builds its botnet by recruiting surveillance cameras.
“The handiwork of the notorious hacker Elit1Lands, this malware uses the AVTech vulnerability, made public back in October 2016,” according to the report. “Security researcher Ankit Anubhav has managed to contact the cybercriminal and learn that so far the botnet has not been used for mass DDoS attacks; yet the author has great expectations about it, especially as Death turned out equally suitable for spam mailouts and spying.”