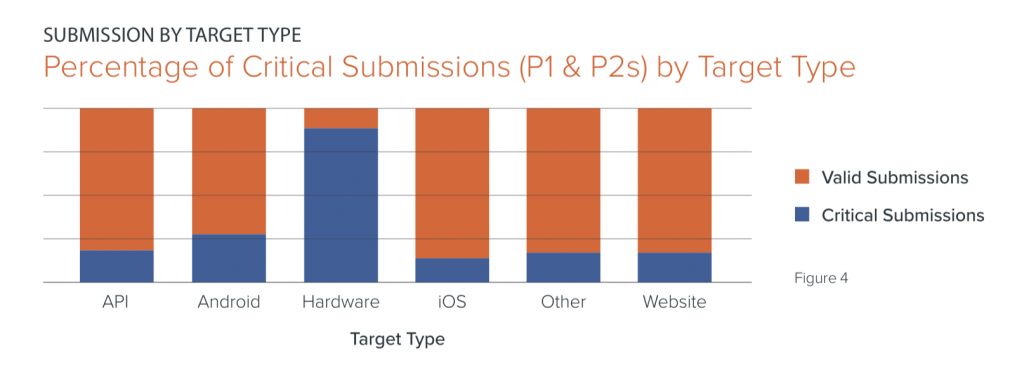
Almost all of hardware vulnerabilities – 90 percent – that were submitted to retail bug bounty programs so far this year were categorized as critical, showing that Point of Sale systems and other retail hardware assets remain a serious security issue.
That’s due to the fact that retail hardware assets often lack built-in security features. Hardware assets often require manual updates (which can’t be done at scale, making it more difficult and time-consuming to patch systems) and are generally short on processing power and memory (meaning standard encryption protocols are frequently forgone by manufacturers), according to Bugcrowd’s 2019 State of Retail Cybersecurity report, released Tuesday. The report looks at the vulnerabilities that have been submitted to retail companies using bug bounty programs on Bugcrowd’s platform.
“Hardware targets… tend to receive fewer submissions, but far outweigh other asset types in percentage of high-impact findings for this industry,” according to Bugcrowd’s report. “Such an imbalance may be the result of programmatic factors unique to each retailer, but there are several macroeconomic factors at play as well.”
Security glitches are most apparent on one of the most popular retail hardware devices, Point of Sale (PoS) devices. PoS systems are connected to the internet and can be searched by hackers that know what to look for systems to act as a doorway to the rest of the network – a security headache that has led to data breaches for retailers like Checkers and Rally and Applebee’s over the past few years.
The difficulty of both security testing and rolling out patches also play into overarching by-design security issues when it comes to retail hardware, researchers said.
“The cost of procuring devices that are essentially treated as disposable testing environments creates a high barrier to entry for many researchers, and tends to reduce overall volume of submissions,” according to Bugcrowd. “On the other hand, dispersed hardware can be difficult to patch, and many newer hardware and IoT devices that were delivered via an accelerated go-to-market strategy in recent years also lack appropriate security testing. Both situations are recipes for potentially high-impact vulnerabilities.”
Top Retail Flaws
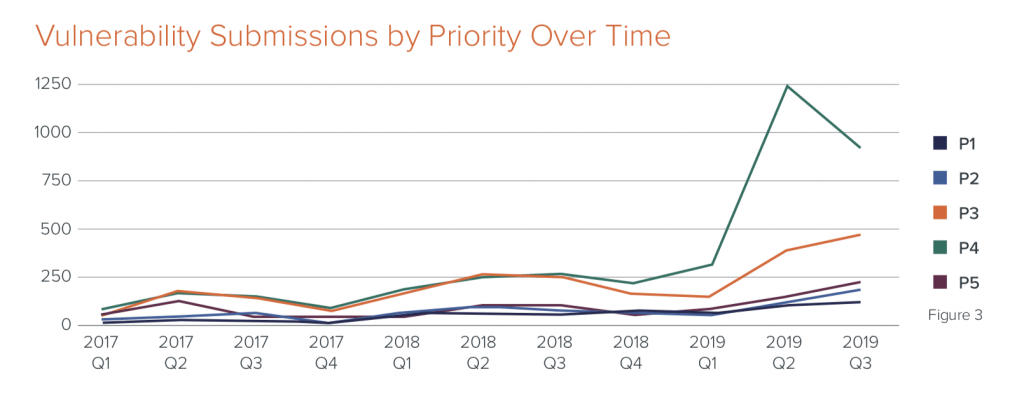
Retail bug bounty submissions have experienced consistent growth since 2017 – but 2019’s first quarter, in particular, saw a bug submission surge that resulted in a 176 percent increase in submitted vulnerabilities.
The explosion is due in part to the first quarter being the end of the traditional “freeze” period- during which lower priority testing and subsequent code changes are postponed.
For the retail industry, the freeze period is around the holiday shopping season, David Baker, CSO of Bugcrowd told Threatpost. “In the runup to the holidays, it is all hands on deck as retailers do almost half their business during this time period,” he said. “This results in the ‘freezing.’ or de-prioritization, of usual activities that are lower priority, such as fixing P5 [non-critical] vulnerabilities. Once the holiday season is over, low-impact vulnerabilities defrost and IT teams prioritize addressing them.”
 Overall, across all retail programs, more than 18 percent of all submissions are critical in severity, with critical retail hardware vulnerabilities weighing into that statistic heavily.
Overall, across all retail programs, more than 18 percent of all submissions are critical in severity, with critical retail hardware vulnerabilities weighing into that statistic heavily.
While retail saw a high volume of bug submissions for flaws in web-based and mobile app surfaces, these were lower-priority flaws, which Bugcrowd said is because web and mobile platforms are “easier” for novice hackers to tackle.
“With a lower barrier to entry, this may be why retail carries a disproportionately high volume of submissions against these asset types versus other industries,” said researchers.
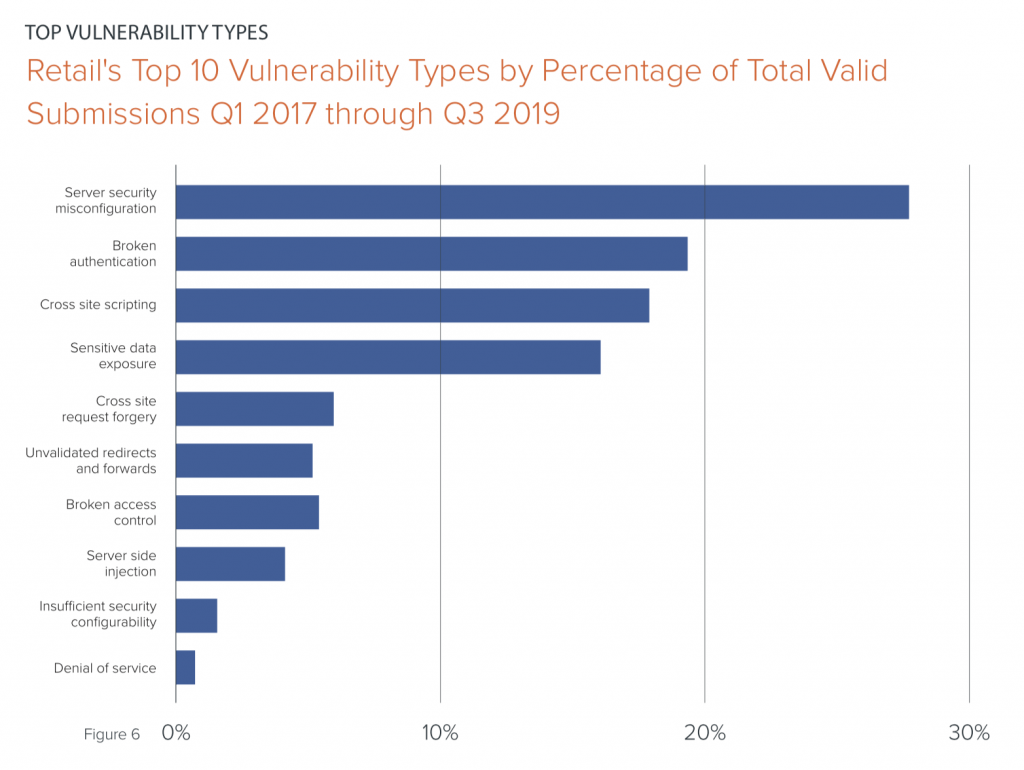
In terms of the most popular retail vulnerabilities, server security misconfigurations and broken authentication take the cake, making up nearly 50 percent of flaws in the retail space.
Misconfigured servers continue to plague companies across various industries, and retail firms are no exception. For instance, in August customers of TGI Fridays Australia were “strongly recommended” to change their MyFridays membership rewards program passwords after the company inadvertently left sensitive loyalty program data exposed on the internet.
Other popular bugs making the top 10 list of total submissions include, cross-site scripting flaws, cross site request forgery, broken access control and more.
“Cross-site scripting is commonly believed to be the predominant vulnerability type uncovered through crowdsourced security programs, but the unique nature of the retail industry demonstrates that this isn’t always so,” researchers said. “While cross-site scripting indeed makes the top ten list at 18 percent of total submissions, nearly 50 percent of vulnerabilities are server security misconfigurations and broken authentication, both of which can range in severity.”
Future of Retail Security
The retail industry still has a ways to go in terms of its adoption of security features. In fact, retail bug bounty programs exhibited a slight slower response time to critical vulnerabilities in 2019 versus the cross-industry average for all public and private programs, according to Bugcrowd.
The volume of submissions in retail tends to be higher which likely plays a factor in a slightly lower response time, Baker told Threatpost. Despite that, Baker said he is optimistic about the future of cybersecurity efforts in the retail space,
“Security and privacy are becoming more important to consumers, so much so that consumers won’t shop with a brand if they’ve suffered a security breach,” he told Threatpost. “We can definitely expect this trend to continue to increase, especially in a post-Cambridge Analytica climate.”
Overall, the security of the retail space is drastically changing due to a couple of emerging factors. Those factors include: A shift in buyer behavior that has consumers looking to “protect and stretch their dollar,” an increased focus on digital transformation, and compliancy laws like GDPR, HIPAA and PCI-DSS (standard for storing and transmitting credit card data post-processing).
These factors collectively are leading retailers to increasingly looking to securing their systems as a way to be a differentiator, said Bugcrowd.
“Crowdsourced security adoption among retailers increased by 50% in the last year, demonstrating that this proactive approach to cybersecurity is one of the more cost-effective models recognized in the industry,” Baker said. “We’re also making good headway tackling ‘Crowd fear,’ as organizations are getting more comfortable working with the security researcher community and want to avoid being the next major headline.”
What are the top mistakes leading to data breaches at modern enterprises? Find out: Join experts from SpyCloud and Threatpost senior editor Tara Seals on our upcoming free Threatpost webinar, “Trends in Fortune 1000 Breach Exposure.” Click here to register.