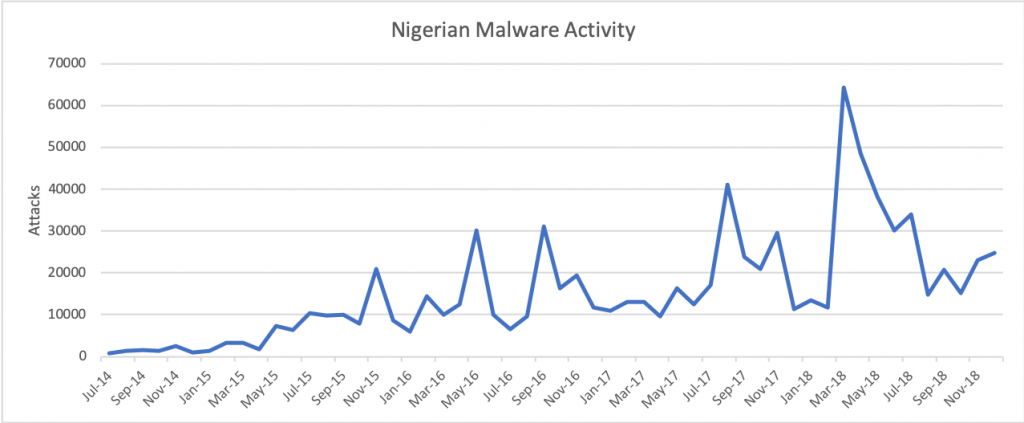
In 2018, Nigeria-based cybercrime jumped 54 percent over the previous year, as groups of scammers expanded their operations adding new tactics and reaching a wider breadth of targets.
The increase, outlined in a report released Thursday by Palo Alto Network’s Unit 42, shows that Nigerian scammers continue to launch attacks at an alarming rate.
Researchers have tracked over 400 Nigerian scam groups, which when combined, attributed to over 51,000 malware samples and 1.1 million attacks over the past four years.
But the past year shows a turning point for Nigerian scam groups, researchers said. Not only were threat actors launching more attacks, but they are also switching to more sophisticated complex malware samples and targeting a wider number of victims in their campaigns, researchers said.
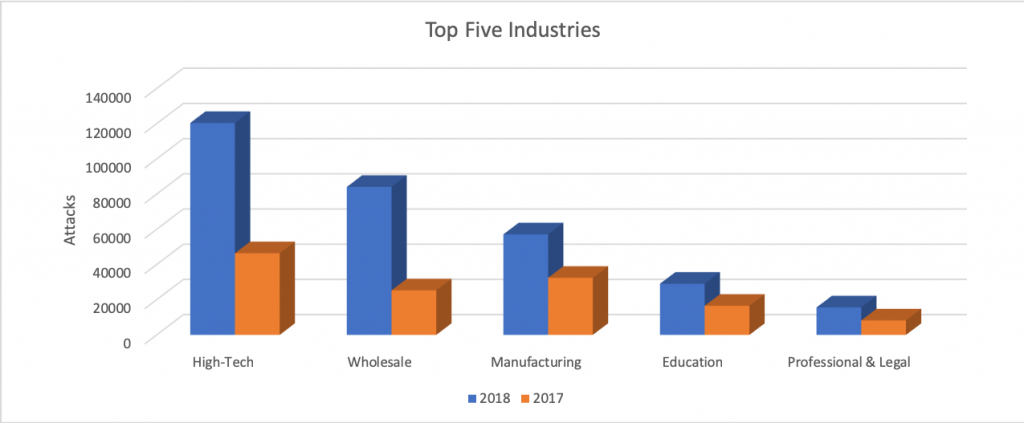
“In 2018, average attacks grew to 28,227 per month with surges in March and April both surpassing previous records,” researchers said. “[Scam] actors remain a formidable threat to businesses worldwide, demonstrating a 54 percent increase in attacks in 2018. These actors predominately rely on email to distribute their malware with the most targeted industries being: High Tech, Wholesale, Manufacturing, Education and Professional/Legal Services.”
BEC campaigns are nothing new – the scams are popular because they involve little to no technical knowledge, malware, or special tools for cyber criminals. Despite that, BEC scams are becoming costlier to impacted victims – a recent report from the FBI said that losses from the attacks almost doubled year-over-year in 2018 to reach $1.2 billion.
Nigerian BEC groups like London Blue, Scarlet Widow are more are continuing to hone their techniques and targets to tap into this lucrative profit, researchers with Agari have pointed out.
New Threats
Nigerian cybercrime groups are turning to from more traditional information stealing malware samples to Remote Administration Tools (RAT). This signals a shift in end goals for many of the attackers: Information stealing malware types are more focused on siphoning critical data; while RATs are commonly leveraged to send malicious or fraudulent emails and access databases within victim organizations in hopes of monetizing their efforts.
While information stealing malware families remain in common use and were primarily used by threat actors in 2017, researchers said that the production of new samples in this type of malware declined 26 percent.
That signals a shift to more RATs, which saw a 36 percent increase, researchers said.
“Combined, the data suggests that Nigerian actors are moving away from legacy information stealers in favor of remote administration tools which provide greater capabilities to achieve their goals,” researcher said.
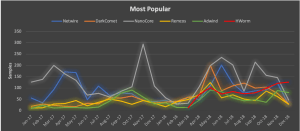
In 2018, the most popular RAT was NanoCore, a modular trojan for which the most recent version was released in March 2015 and made available for sale on the open internet for $25. The RAT is used by the SilverTerrier group. Ironically, the author of the malware, Taylor Huddleston, was arrested and charged with conspiracy in 2017. Nevertheless, the RAT continues to flourish, researchers said.
“This is a fascinating result, given that the developer behind NanoCore was arrested in 2017,” researchers said. “Yet, despite legal efforts to curb its use, a ‘cracked’ version of the tool remains available for free download on various forums across the internet, thus allowing for continued use.”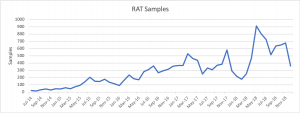
Other top RATs associated with Nigerian scam groups in the past year include: DarkComet, Netwire, HWorm, Remcos and Adwind.
“NetWire, DarkComet, NanoCore, LuminosityLink, Remcos, ImminentMonitor, NJRat, Quasar, Adwind, HWorm are all commodity malware tools that provide attackers with remote access to compromised systems,” researchers said. “In doing so, these tools expand upon the basic data theft capabilities of information stealers and allow [Nigerian scam] actors to modify systems, access network resources, and perform functions on behalf of compromised users.”
New Targets
When it comes to cybercrime, scammers are targeting the high-tech industry the most, with attacks in that segment climbing from 46,000 to 120,000.
“In addition to impressive growth, Nigerian actors continue to launch their attacks against the breadth of all industry segments,” researchers said.
Second-most targeted was the wholesale industry, which saw a 400 percent growth in attacks from 2017; and after that came manufacturing, for which the number of attacks increased from 32,000 to 57,000.
Finally, education and professional/legal services both witnessed sizable growth in attacks as the fourth and fifth most targeted industries, respectively.
Optimistic Future
Despite the barrage of attacks in 2018, Unit 42 researchers remain optimistic about future security measures against Nigerian scam groups due to two areas. Those include an increased awareness and education about email-based attacks across many industries, and more efforts from law enforcement to shut down scam groups worldwide.
For instance, in January 2018 the FBI launched a large-scale effort to dismantle BEC operations globally – dubbed Operation Wirewire – which resulted in the arrest of 74 individuals, including 29 Nigerians.
“Despite the continued growth in attacks and US$12.5 billion in global loses attributed to BEC schemes over the past five years, there were also a series of positive actions that took place cementing 2018 as an important milestone in the battle against this threat,” researchers said,