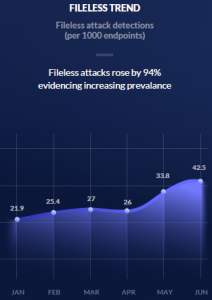
The use of fileless malware in attacks continues to grow and now represents 42 out of 1,000 endpoint attacks, according to an analysis of 2018 data by one security firm. The uptick represents a 94 percent increase in the use of fileless-based attacks between January and June 2018.
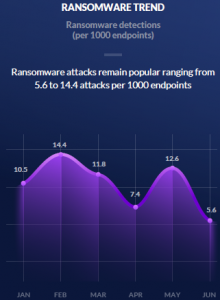
The study, released Tuesday by SentinelOne, also noted rollercoaster fluctuation in the prevalence of ransomware attacks in the same time period. Ransomware attacks represented just over 10 out of 1,000 attacks in January. In February, 14 out 1,000 attacks were tied to ransomware. As of June, ransomware attacks are at an all-time yearly low of 5.1 per 1,000 attacks.
 “Our [report] found that ongoing advancements in fileless malware, PowerShell attacks and ransomware continue to be a pain point as attackers continue to refine attacks to bypass legacy AV,” the report stated.
“Our [report] found that ongoing advancements in fileless malware, PowerShell attacks and ransomware continue to be a pain point as attackers continue to refine attacks to bypass legacy AV,” the report stated.
As the name suggests, fileless malware infects targeted computers leaving behind no artifacts on the local hard drive, making it easy to sidestep traditional signature-based security and forensics tools. Typical attacks exploit vulnerabilities in browsers and associated programs (Java, Flash or PDF readers), or via a phishing attack that entices a victim to click on an attachment. They prey on gullible targets clicking on malicious links or files.
In fileless malware attack scenarios, no files are dropped on the targeted system. Rather, code runs in the computer’s memory and calls on programs already on Windows systems, such as PowerShell and Windows Management Instrumentation (WMI).
Correspondingly, the same study showed attacks that leverage Microsoft’s PowerShell jumped from 5.2 attacks per 1,000 endpoint attacks, compared to 2.5 attacks in May.
 Windows tools, such as PowerShell, are used by adversaries to remain persistent on systems. That’s because fileless malware needs to run code in the targeted system’s random-access memory. Each time the endpoint is restarted the adversary’s in-memory attack ends.
Windows tools, such as PowerShell, are used by adversaries to remain persistent on systems. That’s because fileless malware needs to run code in the targeted system’s random-access memory. Each time the endpoint is restarted the adversary’s in-memory attack ends.
To work around those limitations, attackers often will traverse from one application to another. In some cases, PowerShell will be used to open an application such as Notepad or Calculator in the background, hidden from the user, so the fileless malware can run in one of those application’s memory footprint. Another means of gaining persistence is by loading a PowerShell script that instructs the targeted computer to reconnect to the attacker’s command and control each time the PC started.
So far, this year has seen a number of fileless malware attacks. Kaspersky Lab detailed its discovery in July of the PowerGhost fileless malware/cryptominer. PowerGhost is an obfuscated PowerShell script. First, it plants itself in the targeted system’s random access memory and used the WMI tool and the Mimikatz data extraction tool to escalate privileges and set up its mining operation. More recently, researchers discovered CactusTorch fileless malware that executes and loads malicious .NET files straight via the memory.










