With the U.S. presidential elections looming, bad actors are tapping into the political craze with several malware distribution campaigns, using high-profile political names to tap into victims’ emotions and convince them to click on malicious links.
Researchers have uncovered hundreds of politically-charged malware campaigns – distributing ransomware, remote access trojans (RATs) and more – using the names of prominent political figures like U.S. President Donald Trump, Russia President Vladimir Putin, North Korea ruler Kim Jong-un and more.
“As this investigation has exposed, adversaries will go to any lengths and use anything they deem advantageous, from pop culture to political references — everything is fair game,” Nick Biasini and Edmund Brumaghin, researchers with Cisco Talos, said in a Tuesday analysis, shared with Threatpost ahead of publication. “This is applicable not only to the adversaries delivering malware, but also the miscreants writing tools for adversaries to leverage including crypters, injectors and loaders.”
After investigating a malspam campaign that peddled an executable called “trump.exe,” Biasini and Brumaghin began looking for other types of campaigns leveraging political figures. They found a broad range of applications – some designed to lure victims into paying ransom demands, and others used to gain backdoor access to systems and provide attackers the ability to operate within organizational networks.
The political themes uncovered are not aimed at disinformation – which is another matter altogether that companies like Facebook and Twitter have been grappling with – but rather used as lures aimed to fool victims into clicking or downloading various types of malware, researchers stressed.
RATs
Researchers uncovered a variety of politically themed remote access trojans (RATs) that utilized political themes to trick victims into downloading malware.
For instance, researchers said they came across a RAT that was being delivered via a Word document titled “12 things Trump should know about North Korea.doc,”spread via phishing. (Researchers did not say who specifically was targeted).
At first, when opened on an analysis system the document did not appear to function properly, taking several minutes to load – but after further investigation, it was determined that during that slow opening, Dynamic Link Libraries (DLLs) that were being reconstructed from data present within the document itself, which finally executed malware called Konni RAT. Konni RAT, discovered in 2014, has been used in attacks against government agencies and public organizations linked to North Korea.
Researchers also found political themes in various malicious Excel spreadsheets, including one spreadsheet titled “Trump_administration_economic_indicators_on_China_investments.xls” containing malicious macros that are responsible for infecting systems with the PoisonIvy RAT, which is known for cyberespionage and has been used in attacks with ties to Chine.
Among other politically-motivated themes used to distribute RATs “were [file infecting malware] Neshta, which utilized a theme around North Korean leader Kim Jong-un. Additionally, we found an NjRAT campaign [njRAT is a RAT that may run in the background and silently collect information about the system, connected users, and network activity] that delivered an unusual decoy image. This same image was used as the icon for the executable, aptly named ‘Papa-Putin.exe,'” researchers said.
Iconography
Researchers said that malware such as ransomware, packers (software that unpacks itself in memory when the “packed file” is executed) and crypters (commonly used to attempt to evade antivirus detection by encrypting or obfuscating malicious code associated with malware binaries) were also found using iconography that was associated with Trump.
For instance, researchers found an array of fake ransomware campaigns that featured iconography related to political figures including Donald Trump. Interestingly, the samples didn’t always encrypt the victims’ data properly, or at all, but researchers said they did lead users to believe their data was lost.
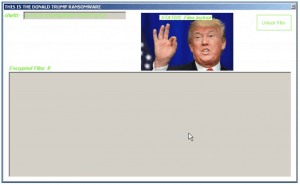
One variant, for instance, appeared to start encrypting files once downloaded and told the victim “This is the Donald Trump ransomware” with an image of Trump.
Another is a ransomware themed around Putin, with the title “Putin Lockware 2.0.” As with most screenlockers, the malware simply removes the icons, taskbar, and task manager on the victim machine and displays the application window displayed above in full-screen mode, researchers said.
“These steps are performed in an attempt to make exiting the application difficult for victims and maximizes the likelihood of a successful ransom payment,” researchers said. “It then directs the user to communicate with the adversary through some means, in this example email, at which point they will demand money to provide the code to ‘unlock’ the screen.”
As the U.S. Presidential Elections draw closer, researchers warned end users to be on the lookout for political name-dropping and iconography used in various malware distribution campaigns – especially via suspicious websites and emails.
“One of the unexpected aspects of the investigation was the presence of lures that dropped malware associated with multiple nation-state attacks in the past, showing how even advanced, sophisticated adversaries will use any means to achieve their nefarious goals,” researchers said. “We were also struck by the wide array of different malware from ransomware and screenlockers, to adware and remote access trojans, and everything in between.”
What are the top mistakes leading to data breaches at modern enterprises? Find out: Join an expert from SpyCloud and Threatpost senior editor Tara Seals on our upcoming free Threatpost webinar, “Trends in Fortune 1000 Breach Exposure.” Click here to register.