The well-known LokiBot malware has popped up in several malicious spam campaigns over the past year, covertly siphoning information from victims’ compromised endpoints. Researchers this week are warning of the most recent sighting of the malware, which was recently spotted in spam messages targeting a large U.S. manufacturing company.
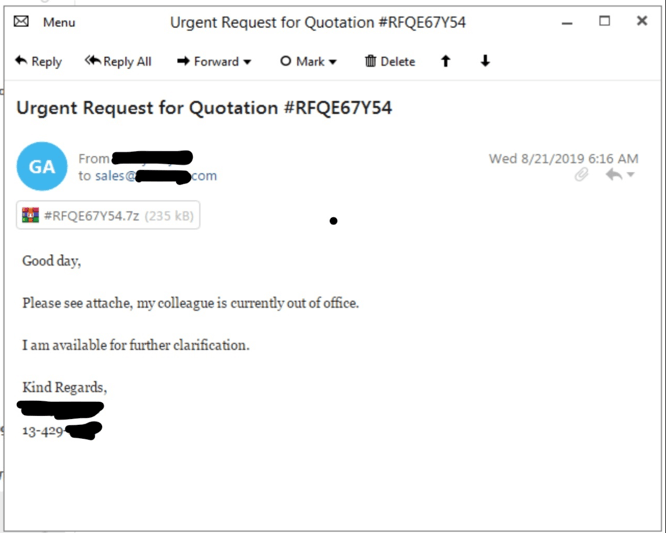
Researchers first discovered the campaign on Aug. 21 after an unnamed U.S. semiconductor distributor received a spam email sent to the sales department from a potentially compromised “trusted” sender. The email, purporting to be distributing an attached request for quotation, was actually harboring prolific trojan LokiBot.
 “The attack is pretty straightforward,” said Fortinet researchers in a Tuesday analysis of the attack. “The LokiBot sample has a file size of 286 KB and was recently compiled on Aug 21, which is coincidentally the same date as when the malicious spam was sent…. The spam email then encourages the user to open the attachment as the senders’ colleague is currently out of office, and at the same time offers the potential victim some assurance that he/she can provide further clarification of the contents within the document if needed.”
“The attack is pretty straightforward,” said Fortinet researchers in a Tuesday analysis of the attack. “The LokiBot sample has a file size of 286 KB and was recently compiled on Aug 21, which is coincidentally the same date as when the malicious spam was sent…. The spam email then encourages the user to open the attachment as the senders’ colleague is currently out of office, and at the same time offers the potential victim some assurance that he/she can provide further clarification of the contents within the document if needed.”
Red Flags
Despite the spam email (titled “Urgent Request for Quotation #RFQE67Y54”) coming from a trusted sender, there were several tell-tale signs that might give away the email as malicious.
While the email is “simple in appearance,” it contained language that appears to be written by a non-native English speaker and contained spelling errors. For instance, the email states, “Please see ‘attache'”, when referring to an “RFQ” (or a “request for quotation”).
Another giveaway is that a closer look at the attached file’s information shows it to be curiously named “Dora Explorer Games,” which is in reference to the children’s’ TV heroine from the show “Dora The Explorer” – a strange name for a file that purports to be related to manufacturing.
“We don’t know if this file info was put in there as a distraction or for reasons unknown to us, as it doesn’t make sense to have such a file name targeting a military and government-based contractor,” researchers said.
Once opened, the file actually harbors LokiBot malware, which is known for stealing a variety of credentials, including FTP credentials, stored email passwords, passwords stored in the browser, as well as a whole host of other credentials.
LokiBot Malware
The malware is known for being simple and effective and for its adoption of diverse attachment types. The malware is a commodity in underground markets, with versions selling for as little as $300.
“LokiBot is distributed in various forms, and has been seen in the past being distributed in zipped files along with malicious macros in Microsoft Word and Excel, or leveraging the exploit CVE-2017-11882 (Office Equation Editor) via malicious RTF files,” said researchers.
LokiBot is also known to be distributed in sneaky ways, including steganography. Several recent attacks in fact showed the malware disguised as a .zipx attachment hidden inside a .PNG file that can slip past some email security gateways, or hidden as an ISO disk image file attachment.
However, in the most recent campaign “this particular sample did not use any steganography as past variants were seen doing,” researchers said.
Connected Spam Campaign
Upon closer investigation, researchers were able to draw loose links between the campaign and a previous spam attack through the IP address.
The IP address of this attack is registered to a webhosting provider in Phoenix, Ariz. (called LeaseWeb USA), which was previously used twice before in malicious spam attacks that occurred in June.
These earlier attacks targeted a large German Bakery in a malicious spam attack trying to lure a victim into downloading an electronic invoice. However, there were key differences between the two spam emails, including language (the previous email was in Chinese).
“Because of the low volume identified, it appears that this IP address may be under the control of one group, and possibly only being used for very targeted attacks,” researchers said. “However, we can only assume this – time will provide a better historical snapshot of campaigns using this IP address.”
To protect against similar future campaigns, researchers urged organizations to both adopt mail solutions as well as train their employees to look out for spearphishing attempts.
“Since it has been reported that this threat has been delivered via social engineering distribution mechanisms, it is crucial that end users within an organization are made aware of various types of attacks delivered via social engineering,” researchers said. “This can be accomplished through regularly-occurring training sessions and impromptu tests using predetermined templates by internal security departments within an organization.”