SAN FRANCISCO – Researchers have discovered several high-severity vulnerabilities in a connected vacuum cleaner. The security holes could give remote attackers the capability to launch an array of attacks — from a denial of service (DoS) attack that renders the vacuum unusable, to viewing private home footage through the vacuum’s embedded camera.
The Ironpie M6, which is available for $230 on Amazon, comes equipped with a corresponding mobile app and a security camera. The vacuum cleaner is built by artificial intelligence home robot company Trifo, and was first launched IronPie at CES 2019. Researchers on Wednesday said that they uncovered six flaws, stemming from the vacuum’s mobile app and its connectivity protocol, at RSA Conference 2020, this week in San Francisco.
“The most severe vulnerability allows attackers to access any video stream from any Trifo device across the world,” Erez Yalon, director of security research with Checkmarx, told Threatpost. “Through this vulnerability, every single user – whether in a home or office setting as shown in our PoC video – is at risk of a hacker obtaining a live video feed. Needless to say, this represents a total loss of privacy.”
The device’s manufacturer, Trifo, has so far not responded to attempts to report the vulnerability starting on Dec. 16, 2019 – and as of publication, the flaws remain unpatched, Yalon said. Threatpost has also reached out to Trifo multiple times for comment regarding the vulnerabilities.
“Complicating the situation further, since Trifo has not issued a fix, the only risk mitigation options for device owners are either covering the camera or cutting off the vacuum’s access to Wi-Fi, thereby reducing some of its key features,” Yalon told Threatpost.
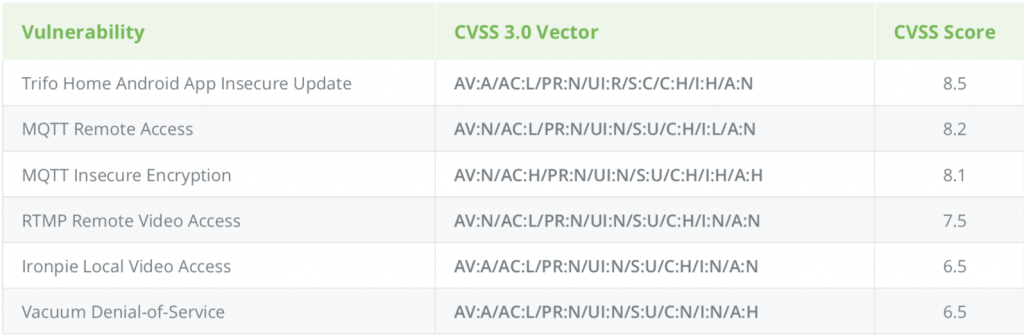
The most severe vulnerability discovered exists in Trifo’s Android app, called Trifo Home. This flaw has an 8.5 out of 10 on the CVSS 3.0 scale, making it high-severity. Trifo Home uses an HTTP request when the application queries the service for a new APK (Android application package), which is the package file format used by the Android operating system for updating the app.
Because requests are being sent via HTTP, it means they are in plaintext, and anyone monitoring the connection can read them. Using a Burp Suite proxy server (a web application security tool), attackers could easily monitor – and tamper with – the requests in transit. They could then take it a step further and trick the app into installing a malicious, attacker-controlled APK – ultimately allowing them to install malware on the mobile app.
Researchers also found high-severity flaws stemming from the vacuum’s implementation of MQTT, an IoT connectivity protocol, used as a bridge between the vacuum, the backend servers, and the Trifo Home app. Researchers said that the way MQTT has been implemented in the Ironpie M6 lacks proper authentication mechanisms; it connects to the MQTT servers via an unencrypted connection (the MQTT payload is only encrypted after packets are exchanged) and data is transferred in clear text.
This lack of authentication means that a remote attacker can monitor traffic coming to and from the Ironpie M6, its corresponding app and the servers. Making matters worse, the app uses a fixed, hardcoded username and password in the APK, making it easily accessible; And, the app connects to the server using a certificate inside its APK, which can easily be fetched via attackers who are monitoring the traffic.
“With the certificate, which can be easily fetched from the APK, and the username/password being hardcoded and always the same, an attacker can connect to the MQTT servers, impersonating any client ID. In addition, the IDs are generated sequentially and are easily guessable,” said researchers.
Once they use this attack to obtain the vacuum client ID (the ID used to identify the vacuum), attackers can then connect to the MQTT servers using the ID – allowing them to take full control of the vacuum. After taking control of the vacuum, attackers can then carry out an array of attacks, including viewing the video feed on the vacuum, as well as crashing the vacuum cleaner (via specially crafted data packets sent via port 7000).
Though more light has been shed around insecure Internet of Things (IoT) devices – as well as more calls for regulation– connected devices themselves continue to be insecure, Yalon said. This opens up concerns for end users from privacy threats stemming from smart home devices, to botnets evolving to launch stronger and larger Distributed Denial of Service (DDoS) attacks on vulnerable connected devices worldwide.
“While the privacy issues with Trifo devices are clearly concerning, the bigger topic that needs to be addressed revolves around bringing connected devices into our personal, private environments – especially ones embedded with cameras and microphones. As we continue to prioritize convenience in our day-to-day lives via devices like this smart vacuum, consumers must recognize, understand, and address as best as possible the corresponding security risks. The device manufacturers themselves must also place a higher emphasis on the security of today’s consumer-facing devices,” Yalon told Threatpost.
For Threatpost’s complete RSA Conference 2020 reporting, please visit our special coverage section, available here.