 UPDATE — DNS hijacking attacks carried out today against the home pages of Google, Yahoo and other high-profile sites in Romania have been traced to an attack on the Romanian Top Level Domain Register, researchers at Kaspersky Lab said.
UPDATE — DNS hijacking attacks carried out today against the home pages of Google, Yahoo and other high-profile sites in Romania have been traced to an attack on the Romanian Top Level Domain Register, researchers at Kaspersky Lab said.
“The altered DNS records propagated from there to different Internet Service Providers’ DNS services, including Google’s,” Kaspersky said in a statement.
Visitors trying to reach Google, Yahoo, Microsoft, PayPal and others in Romania were redirected to a page on which an attacker who said he was from Algeria claimed responsibility for the hack.
The hack resulted in the respective being defaced and redirected. On the defacement, the attacker simply claimed to be Algerian and said “to be continued…”. Site defacements such as this have been common for more than a decade now, and hackers often brag about new defacements on various sites that track such attacks. But it’s relatively rare for a major site such as Google or Yahoo to fall victim to a defacement like this.
Stefan Tanase, a senior security researcher at Kaspersky Lab, said the attack likely was accomplished via DNS poisoning.
“All we know is that Google’s public DNS servers (8.8.8.8 and 8.8.4.4) were resolving requests for google.ro and other major .RO websites to the IP address hosting the defacement page,” Tanase said. “This basically means that everyone using Google’s public DNS servers in their network configuration could not access these domains. The problem gets even worse when you factor in that many organizations and even country-wide ISPs are relying on Google’s DNS servers to resolve requests.”
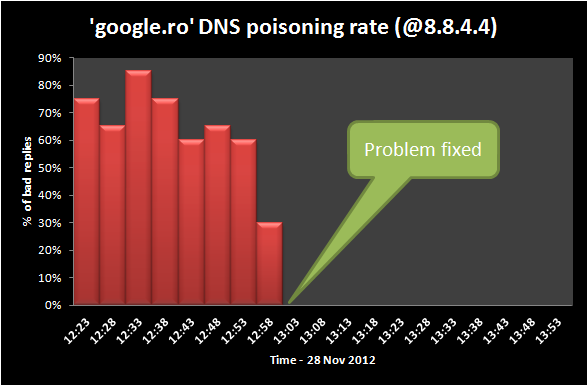
A DNS cache poisoning attack can be done in a couple of ways, but the end result is that users who attempt to go to a site such as Google.ro will be redirected to a site controlled by the attacker. One common method for these attacks is for the attacker to spoof the IP address of the target site’s DNS servers and then enters an address for a server he controls. He can then direct victims to his server and deliver whatever content he chooses.
In an analysis of the attack, Tanase, who is based in Romania, said that it could have turned out much worse, had the attacker decided to serve malware or a page designed to capture user credentials for Gmail or another important service.
“In this case, the good part is that it was just an ordinary defacement. It could’ve been much worse if the attacker distributed an exploit kit or a phishing page to all the victims,” he said in an email interview.
Google appears to be repairing the compromised DNS records at the moment, and both of the affected servers were back to serving the correct home page as of about 6 am EST, Tanase said. However, the attack is still ongoing for the PayPal.ro domain at the moment.
This article was updated on Nov. 28 to include information on the attack against Romania’s TLD register.









