Cryptowall has gotten a minor, but important facelift that might make it more difficult for researchers to tear apart and for victims to recover their encrypted data without paying a ransom.
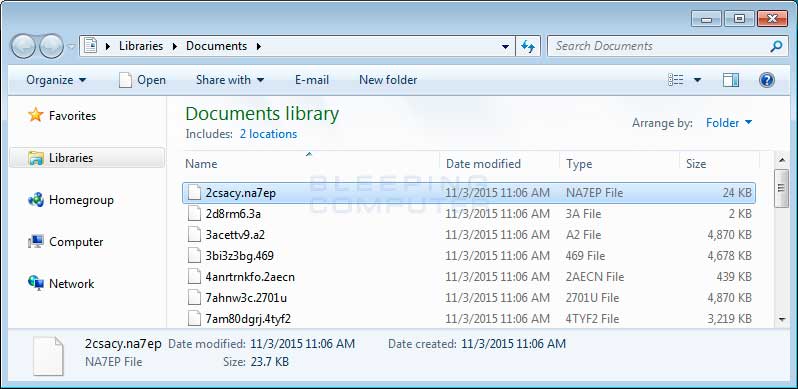
Spotted two days ago, the latest update to the ransomware has begun not only encrypting data on victims’ machines, but also file names, a first according to independent researcher Nathan Scott, who examined the code along with researchers from Bleeping Computer.
“I’m surprised more don’t it; this makes it significantly harder to recover files except for paying the ransom,” Scott said. “If you try to do a forensic data recovery, the files show up with these weird names and the user doesn’t know what file is what. No one knows any structure in files any more.
“The only way to regain your data is a complete backup,” Scott said. “If you don’t backup, the only way to get the data back is to pay the ransom.”
The attackers behind Cryptowall have also updated the ransom note that victims are presented with. The note contains new mocking language, congratulating the victim for becoming part of the Cryptowall community, and the attackers have also assigned themselves a hashtag #CryptowallProject. The use of the hashtag, Scott speculates, is that victims may use it to commiserate on social media and if there is any kind of volume, it may lead them toward paying the ransom that much quicker.
Cryptowall is by far the most profitable of the ransomware families. A recent report from the Cyber Threat Alliance, a consortium of security vendors, concluded that Cryptowall 3.0 has caused an estimated $325 million in damages. It’s unclear whether this most recent version of the crypto-ransomware is indeed Cryptowall 4.0, as Bleeping Computer has called it, or a point release as others have labeled it.
@Techhelplistcom @jedisct1 technically they don't call it 4.0 😉 they removed the version in their dropped note pic.twitter.com/HSNcJBn7Rb
— Yonathan Klijnsma (@ydklijnsma) November 4, 2015
Regardless, this version of Cryptowall spreads via infected email attachments as its predecessors have. The attachments are disguised as a Word document (usually pretending to be an invoice or business document), but are instead a JavaScript executable that launches the malware.
This version also includes a nasty little feature where a compromised machine is less likely to have its restore points intact, making recovery that much harder. Restore points are system snapshots taken by Windows every time programs are installed or Windows is updated.
“Sometimes with ransomware, the user is lucky and the malware does not remove restore points or fails to and you can restore the system to a date before the ransomware infection and restore it as if it never happened,” Scott said. “4.0 ensures this isn’t an option.”
Scott said that most victims who choose to pay the ransom in order to restore their data are sent the private key from the attackers, which isn’t always the case with every ransomware operation.
“They run their model like a business and it’s very straightforward how it works. They know if they screw over too many people, they’re not getting paid,” Scott said. “They go out of their way make sure victims get files back.”
The FBI has also suggested that victims might want to consider just paying the ransom, especially for Cryptowall infections. The FBI’s estimates of Cryptowall damages were much lower than the CTA’s ($18 million).
“These guys have been around the longest,” Scott said, “and have learned from their mistakes.”