There have been many disruptive innovations
in the history of modern computing, each of them in some way impacting
how we create, interact with, deliver, and consume information. The
platforms and mechanisms used to process, transport, and store our
information likewise endure change, some in subtle ways and others
profoundly.
Cloud computing is one such disruption
whose impact is rippling across the many dimensions of our computing
experience. Cloud – in its various forms and guises — represents the
potential cauterization of wounds which run deep in IT; self-afflicted
injuries of inflexibility, inefficiency, cost inequity, and poor
responsiveness.
But cost savings, lessening the
environmental footprint, and increased agility aren’t the only things
cited as benefits. Some argue that cloud computing offers the potential
for not only equalling what we have for security today, but bettering
it. It’s an interesting argument, really, and one that deserves some
attention.
To address it, it requires a shift in perspective relative to the status quo.
We’ve been at this game for nearly forty
years. With each new (r)evolutionary period of technological
advancement and the resultant punctuated equilibrium that follows,
we’ve done relatively little to solve the security problems that plague
us, including entire classes of problems we’ve known about, known how
to fix, but have been unable or unwilling to fix for many reasons.
With each pendulum swing, we attempt to pay
the tax for the sins of our past with technology of the future that
never seems to arrive.
Here’s where the notion of doing better comes into play.
Cloud computing is an operational model
that describes how combinations of technology can be utilized to better
deliver service; it’s a platform shuffle that is enabling a fierce and
contentious debate on the issues surrounding how we secure our
information and instantiate trust in an increasingly open and
assumed-hostile operating environment which is in many cases directly
shared with others, including our adversaries.
Cloud computing is the natural progression
of the reperimeterization, consumerization, and increasingly mobility
of IT we’ve witnessed over the last ten years. Cloud computing is a
forcing function that is causing us to shine light on the things we do
and defend not only how we do them, but who does them, and why.
To set a little context and simplify
discussion, if we break down cloud computing into a visual model that
depicts bite-sized chunks, it looks like this:
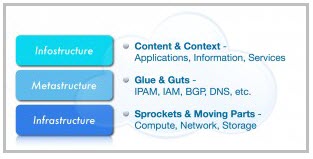
At the foundation of this model is the infrastructure layer that
represents the traditional computer, network and storage hardware,
operating systems, and virtualization platforms familiar to us all.
Cresting the model is the infostructure
layer that represents the programmatic components such as applications
and service objects that produce, operate on, or interact with the
content, information, and metadata.
Sitting in between infrastructure and
infostructure is the metastructure layer. This layer represents the
underlying set of protocols and functions such as DNS, BGP, and IP
address management, which “glue” together and enable the applications
and content at the infostructure layer to in turn be delivered by the
infrastructure.
We’ve made incremental security progress at
the infrastucture and infostructure layers, but the technology
underpinnings at the metastructure layer have been weighed, measured,
and found lacking. The protocols that provide the glue for our fragile
Internet are showing their age; BGP, DNS, and SSL are good examples.
Ultimately the most serious cloud computing
concern is presented by way of the “stacked turtles” analogy: layer
upon layer of complex interdependencies predicated upon fragile trust
models framed upon nothing more than politeness and with complexities
and issues abstracted away with additional layers of indirection. This
is “cloudifornication.”
The dynamism, agility and elasticity of
cloud computing is, in all its glory, still predicated upon protocols
and functions that were never intended to deal with these essential
characteristics of cloud.
Without re-engineering these models and
implementing secure protocols and the infrastructure needed to support
them, we run the risk of cloud computing simply obfuscating the
fragility of the supporting layers until the stack of turtles topples
as something catastrophic occurs.
There are many challenges associated with
the unique derivative security issues surrounding cloud computing, but
we have the ability to remedy them should we so desire.
Cloud computing is a canary in the coal mine and it’s chirping wildly. It’s time to solve the problems, not the symptoms.
This essay originally appeared on the Microsoft TechNet Blue Hat blog.










