Do threat actors carry out phases of their attack on different days of the week? Do threats use the same infrastructure for exploitation and control? These may not be the sort of questions that cybersecurity professional usually think about, but their implications can actually have an important impact of how to better align resources and strategies to detect and defend against attacks.
For the Q1 2019 Threat Landscape Report, threat analysts at FortiGuard Labs were given leeway to roam across the threat landscape they work with daily and share some stories of interest from their cyber threat data that did not necessarily relate to the primary topics or flow of the main report. This quarter, they chose to dig into data from the company’s web filtering service.
Here is what they found.
What and Why
Weekdays vs weekends. Researchers wanted to see if threat actors conduct phases of their attacks on different days of the week to further demonstrate that cybercriminals are always looking to maximize opportunities. When they compared web-filtering volume from two Cyber Kill Chain phases during weekdays and weekends, they discovered that pre-compromise activity is roughly three times more likely to occur during the work week.
This is largely due to the fact that pre-compromise activity requires someone to click on a phishing email or perform some other action, whereas post-compromise activities that rely on command-control services do not have this requirement and can occur anytime. Cybercriminals understand this, work to maximize opportunity during the week when Internet activity is taking place.
The web filtering service blocks and then logs attempts to access malicious, hacked, or inappropriate websites. Analysts have applied various categorizations to this activity, like the type of website being sought and the phase of the Cyber Kill Chain in which it occurs.
The overwhelming majority of blocks in Q1 occurred in the exploit (initial attack) and control (manipulation of data) phases. This stands to reason, given that devices visiting these malicious URLs are often directed there (e.g. via phishing) for the purpose of exploitation and/or for ongoing command-and-control instructions after successful exploitation.

Comparison of web filtering volume for two Cyber Kill Chain phases during weekdays (blue) and weekends (orange).
In the figure below, the contrast is clear between pre- and post-compromise activity over the quarter. The blue dots signify weekdays and orange dots weekends.
WWWW
Every bit of knowledge that can be gained on how attackers work offers at least some improvement over the baseline. In this case, it may make sense to consider differentiating weekday and weekend filtering practices and in prioritizing threat discovery activities.
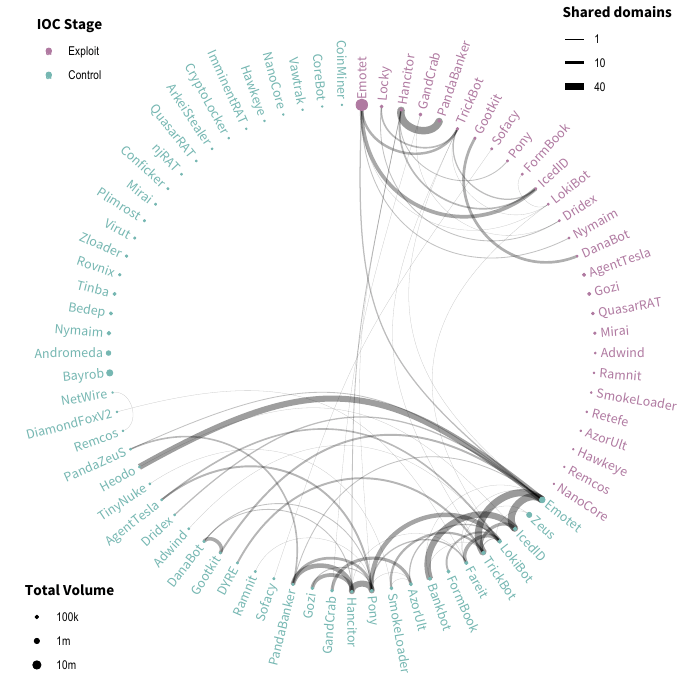
Shared infrastructure. An additional aspect of the web filtering data that researchers found worthy of attention was the degree to which different threats shared infrastructure (namely, URLs). The figure below displays this overlapping infrastructure in a circular network diagram. Each node represents malware or botnet communication activity generated by threats during the control stages of the Kill Chain. The thickness of lines represents the number of domains shared between threats at each stage. The size of each node corresponds to the total volume detected in Q1. This data fuels several interesting observations.
For instance, some threats appear to leverage this community-use infrastructure to a greater degree than unique or dedicated infrastructure. In fact, nearly 60% of all analyzed threats shared infrastructure. IcedID, the #9 threat by volume in the web filter data this quarter, offers a good example of this “why buy/build when you can borrow” behavior. Like so many others, it shared nearly two-thirds of the domains it contacted with other threats.
Finally, and perhaps most intriguing: when threats share infrastructure, they also tend to do so within the same stage in the Kill Chain. Similarly, while many different threats may share the same domain during the exploitation phase of an attack, it would be unusual for that threat to leverage a domain for exploitation and then later leverage it for C2 traffic.
Security Tactics for People, Processes and Technology
Attack vectors, like the ones just discussed, underscore the need for organizations to rethink their strategy to better future-proof and manage cyber risks. An important first step involves treating cybersecurity more like a science – doing the fundamentals really well – and then implementing an intentional layered strategy that uniquely covers all aspects of the network.
As IT teams seek to create a layered security environment, there are several tactics they should consider:
People – Training makes the difference between employees being an organization’s critical front-line cybersecurity asset or its greatest liability. Employees need to be trained in basic cyber hygiene practices like creating strong passwords, not reusing or sharing those passwords, identifying illicit urls and email sources, and not clicking links in emails from unknown senders. IT teams can also improve cybersecurity at the employee level with access management policies, such as the implementing the principle of least privilege.
Processes – IT security teams should have a cyber incident response plan in place. They should also not only ensure that proper backups are taking place and being stored off-network, but that those backups are regularly being tested. The collection, analysis, and sharing of threat research across teams, devices, and network environments is also critically imperative. Finally, IT teams must know what assets are online, where those assets are, and then be able to prioritize their access to and consumption of resources based on which are most business-critical.
Technology – It’s important for IT teams to not implement isolated point solutions as they layer their defenses, but instead choose tools based on their ability to be integrated and automated so they can share real-time threat intelligence. This integrated approach creates a comprehensive solution that can facilitate rapid detection and mitigation of threats across the entire distributed network. Deception technology is another tactic IT teams should make use of. Effective deception strategies make it harder for an adversary to determine which assets are fake and which are real, while tripwires embedded in these false signals increase the ability to detect an intruder. Finally, segmenting corporate networks limits exposure of critical data if there is a breach.
Adapting Security Strategy
Last quarter offered insight into how attackers are currently operating and how they continue to evolve. For example, different stages of their attacks occur on different days, and they tend to share infrastructure. In response, IT security teams can be on the lookout for these activity identifiers and adjust their detection and filtering practices accordingly. It is also clear that building a layered defense approach that factors in people, processes, and technology will minimize the impact of such attacks, even as they continue to evolve.
(Derek Manky is Chief of Security Insights and Global Threat Alliances at Fortinet. He has more than 15 years of cybersecurity experience and helps customers formulate security strategy.)