In addition to the many tweaks and new features in Google’s Android 8.0 Oreo operating system introduced last month, the biggest changes are its security enhancements.
Oreo security additions are meaningful and go far beyond what recent OS updates have brought to the table.
With Android Oreo (referred to as simply O), Google has elevated security, introducing important device hardening such as Project Treble, System Alerts, device permissions and Verified Boot.
“With Android O, Google introduces a major re-architect of the Android OS framework,” said Kyle Lady, senior research and development engineer at Duo Security. “There are some big changes that will impact users, developers and device manufacturers for years to come.”
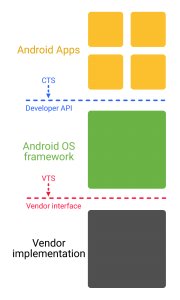
Mobile security experts point to the introduction of Project Treble in O as a major security milestone for Google. Project Treble is Google’s revamp of the Android OS framework—separating the vendor implementation (device-specific, lower-level software written by third-party manufacturers) from the Android OS framework.
One of the goals of Project Treble is to streamline the often maligned Android patching process that security experts say is one of the weakest links in Android security defenses. According to Google’s Android Security 2016 Year In Review, more than half of Android devices haven’t received a security update in the past year.
Project Treble
 Project Treble aims to remedy that by making it easier, faster, and cheaper for OEMs and components manufacturers to send out Android updates.
Project Treble aims to remedy that by making it easier, faster, and cheaper for OEMs and components manufacturers to send out Android updates.
Project Treble separates the hardware-specific drivers and firmware used by companies such as Samsung or Qualcomm from the Android operating system. The implications will be significant when it comes Google’s ability roll out OS patches without having to wait for things such as chipset compatibility. Google said by creating this modular base for Android, it will be able to support updates moving forward on older hardware that OEM partners may no longer support.
“Project Treble is part of a long term strategy that is going to help out all the Android OS stakeholders well past this latest OS release,” said Andrew Blaich, security researcher at Lookout.
With Project Treble, Google puts the Android OS framework and vender-specific implementations into different processes that communicate with each other using a standard vendor interface. The vendor interface will be maintained from version to version which means the new Android OS framework will run with minimal changes on top of an older device.
Android Compartmentalization
That strategy of segmenting parts of the Android platform and allowing for more efficient component management and better vulnerability containment should something go awry, is another meaningful part of Project Treble and part of an ongoing strategy by Google to reduce Android’s attack surface.
“Attack surface reduction means several different things. How do we make sure an application can only do what it is intended to do? How do we minimize the surface that is exposed? How do we contain processes within Android and follow the principle of least privilege?” said Nick Kralevich, head of Android platform security at Google at a recent Black Hat talk.
For a long time, Google approached security differently, focusing on exploit mitigations such as fstack-protector and ASLR, and preventing format string vulnerabilities. Those days are over.
By further reducing the attack surface in Oreo, Google believes it is taking a smarter approach to stopping the next Stagefright-like vulnerability.
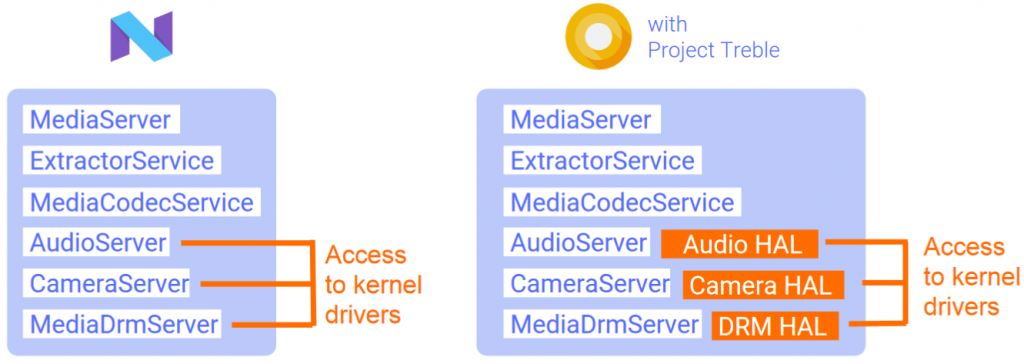
In the old model, hackers were able to achieve remote code execution via MediaServer by bypassing SELinux with chained vulnerabilities. That changed in Android 7 (Nougat), where MediaServer functionality split into seven components such as MediaExtractor and MediaDrmServer, preventing format string vulnerabilities.
In Project Treble, Google accelerates the compartmentalizing of components and has introduced a bevy of new hardware abstraction layers (HALs) for the audio, camera and DRM servers inside the media framework. With those HALs in place more pieces of the Android framework are isolated in separate processes and sandboxes and no longer have access to the OS kernel—making it harder for hackers to chain vulnerabilities and compromise an Oreo device.
Kernel Lockdown
The reduction of user space attack surface has shifted focus by bad guys and researchers alike to finding vulnerabilities in the Android kernel. In 2014, Google said, kernel bugs represented four percent of reported bugs compared with 39 percent today.
To address that shift, Android O limits access to the kernel via the introduction of a seccomp filter. Seccomp (short for secure computing mode) is a security feature that filters system calls to the kernel using a configurable policy. Google said it found that shutting down unused system calls reduced the kernel attacks.
“In Android-powered devices, the kernel does the heavy lifting to enforce the Android security model. As the security team has worked to harden Android’s userspace and isolate and deprivilege processes, the kernel has become the focus of more security attacks,” wrote Paul Lawrence, security engineer with the Android development team, earlier this year.
Seccomp makes unused system calls inaccessible to application software. Because these syscalls cannot be accessed by apps, they can’t be exploited by potentially harmful apps, Lawrence said.
Better App Management and Controls
With Oreo, Google is also rethinking app permissions and scaling back what they are allowed to do.
One of the most common ways attackers try to exploit a device is by building malware into an application. Despite the fact Google does a lot of verification on its Play Store to ensure no malware is present in applications, users can side-load an application from a third-party app store.
In order to side-load an app, a user must first permit the installation of apps from “unknown sources” via a checkbox. That permission has been an all or nothing choice—allow one unknown third-party and allow them all.
Oreo changes this, allowing users to set permissions on a per-app basis, instead of globally allowing all applications to install if the checkbox is enabled. That means should a drive-by download attempt to be installed on a device, a user will forced to decide whether they want to download it and what it’s permissions should be.
System Alert
As part of Android O’s reeling in of app permissions, Google said it will also beef-up security on its System Alert window functionality. The System Alert feature allows developers to create apps that can pop-up or display windows on top of all other Android apps running on a handset.
This feature has been abused by malicious developers who create what users think are a persistent window on their Android device. Victims are asked to pay a ransom to make the window go away or are tricked into inputting credentials in hacker controlled text fields. In Android O, System Alert overlays will include visual notifications that can be clicked on to remove the overlay.
Verified Boot System
Android has had a Verified Boot system since 2013 that would check a user’s software as it loaded the OS for vulnerabilities.
Now with Oreo, Verified Boot goes a step further and prevents users or hackers from booting to older more vulnerable versions of the OS an adversary may have rolled the system back to.
The feature also supports the ability for apps and mobile device management firms to secure hardware areas of an Android device upon boot. That allows both to guarantee that the system has passed a Verified Boot check to ensure the device has a specific patch, for example, before granting user access to a banking app or enterprise resource.
Better, More Secure Protocols
Looking past features, Lookout’s Blaich said he is impressed with Oreo’s attention to deprecating the use of older insecure protocols for network connections. “The use of SSLv3 for secure HTTPS connections is being discontinued, this prevents the device and its apps from using a known insecure protocol that could leak sensitive data,” he said. He added, Google has also hardened certain network connection APIs from not falling back to older TLS versions that can leak sensitive data.
Reaping The Rewards
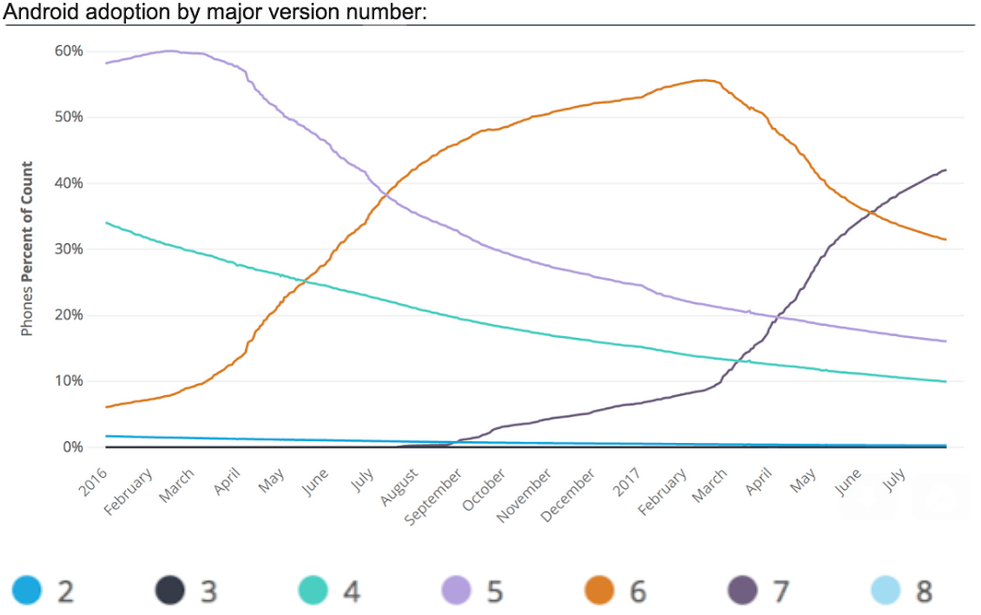
Right now, Android Oreo is only available on a handful of Google Pixel smartphones. According to Google, over the next six months O will pushed out to third-party flagship handsets made by Samsung, LG and HTC. But it could take years for the benefits of Android O benefit the masses. That’s because of slow adoption rates of Android operating systems. Android 7.0 (Nougat) was introduced in Aug. 2016 and a full year after its release it’s just now used on half of Android devices, according to Duo Security.
“Android O is a big step forward,” said Duo Security’s Lady. He said with O, Google closes the security gap on the iPhone. “It used to be if you cared about security you had to pay a premium and buy an iPhone. Soon, even a $50 Android device running O will be on par with a $1,000 iPhone X when it comes to security.”