 The Wikileaks Website labored under a massive denial of service attack Tuesday, 48 hours after the site published its first installment of a massive trove of leaked U.S. diplomatic cables.
The Wikileaks Website labored under a massive denial of service attack Tuesday, 48 hours after the site published its first installment of a massive trove of leaked U.S. diplomatic cables.
Both Wikileaks.org and cablegate.wikileaks.org, the subdomain created to host the leaked U.S. embassy cables were both reachable Tuesday afternoon. However, Internet monitoring firms confirm that the site has been the target of multiple distributed denial of service (DDoS) attacks since posting the documents on Sunday.
The first attack, delivering 2-4 Gigabits of traffic per second, began on Sunday, November 28th, knocking the site offline for several hours on Sunday, according to the firm Netcraft. Those attacks continued on Tuesday, causing intermittent interruptions in availability for the site, Netcraft said.
Around 9:30 AM on Tuesday, a note posted on Wikileaks Twitter feed announced that the latest attack has exceeded 10 Gbps. UK-based Internet security firm Netcraft reported that the site went down temporarily Tuesday but has since returned to service.
Threatpost reported Monday that Wikileaks managed to skirt the DDoS attack by serving up its Website from a revolving list of three different servers and by moving from the France-based Octopuce to the more robust Amazon Web Services infrastructure.
The source of the attacks is unknown. A hacker-activist calling himself ‘The Jester’ (Twitter handle @th3j35t3r) has claimed responsibility for the first attack, explaining that the DDoS was retribution for Wikileaks “attempting to endanger the lives of our troops, other assets, and foreign relations.”
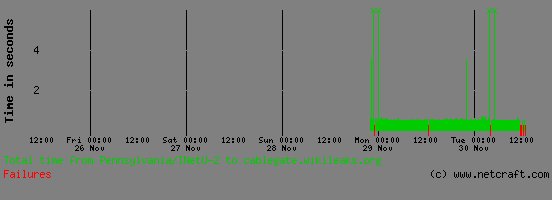
Arbor Networks noted in a blog post that their profile of the attack is consistent with the Jester’s claim to have used application layer attacks to create a denial of service with lower levels of traffic. However, individuals and governments with an interest in snuffing out Wikileaks are legion, and there has been no independent verification of The Jester’s claims.
In other news, Reuters reports that the South American Republic of Ecuador has offered Wikileaks founder Julian Assange a safe haven to lecture and teach. Assange’s whereabouts are unknown. Assange has faced harsh criticism from the U.S. and its allies for releasing the diplomatic cables, most of which date to the post 9-11 era, and which have complicated the U.S.’s relationships with its allies. The source of the documents is unknown, however a former Army Intelligence officer, Bradley Manning, is under arrest for the unauthorized disclosure of classified intelligence, part of which is believed to be the 250,000 diplomatic cables that were leaked to Assange and Wikileaks.
service attack Tuesday, 48 hours after the site published its
first installment of a massive trove of leaked U.S. diplomatic
cables.
Both Wikileaks.org and cablegate.wikileaks.org, the subdomain
created to host the leaked U.S. embassy cables were both
reachable Tuesday afternoon. However, Internet monitoring
firms confirm that the site has been the target of multiple
distributed denial of service (DDoS) attacks since posting the
documents on Sunday.
The first attack, delivering 2-4 Gigabits of traffic per
second, began on Sunday, November 28th, knocking the site
offline for several hours on Sunday, according to the firm
Netcraft. Those attacks continued on Tuesday, causing
intermittent interruptions in availability for the site,
Netcraft said.
Around 9:30 AM on Tuesday, a note posted on Wikileaks Twitter
feed announced that the latest attack has exceeded 10 Gbps.
Arbor Networks is reporting that the site went down
temporarily but has since returned to service.
Threatpost reported Monday that Wikileaks managed to skirt the
DDoS attack by serving up its Website from a revolving list of
three different servers and by moving from the France-based
Octopuce to the more robust Amazon Web Services
infrastructure.
The source of the attacks is unknown. A hacker-activist
calling himself ‘The Jester’ (Twitter handle @th3j35t3r) has
claimed responsibility for the first attack by tweeting “TANGO
DOWN” followed by an explanation for his attack, “…for
attempting to endanger the lives of our troops, other assets,
and foreign relations.” Arbor Networks noted in a blog post
that their data on the attack are consistent with the Jester’s
claim to use application layer attacks to create a denial of
service with lower levels of traffic. However, individuals and
governments with an interest in snuffing out









