When it comes to the next generation of mobile networks, 5G promises a more Internet of Things-friendly ecosystem with vast improvements over the current capabilities of 4G – however, its intersection with IoT will also raise the stakes on cybersecurity.
The benefits of 5G are myriad: Not only will it allow extremely fast data feeds of 1Gbps and better (equivalent to top-tier home broadband speeds), but 5G also offers ultra-low latency (less than one millisecond according to the standard). It also supports greater density (up to 100 times more connected devices per unit area, all of them getting the same speed and latency) and better network energy usage.
To that latter point, the 5G standard calls for a 90 percent reduction in energy consumption, which translates into low-power IoT devices in industrial environments boasting 10 years’ worth of battery life.
Taken together, this opens up new use cases. Ultra-low-latency for example makes it possible to support self-driving cars; IoT sensors on autonomous vehicles will be able to measure temperature, traffic conditions, weather, GPS location, distance to other objects, and so on in real-time.
Similarly, in the medical field, applications like remote-controlled surgery for rural areas can potentially change the face of medicine. And, in industrial IoT, tracking sensors throughout the supply chain can support real-time water delivery, streamlined waste management, live traffic monitoring and light changes, and even on-demand electrical grids.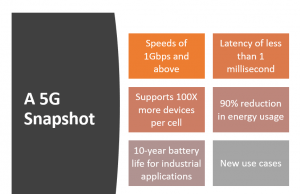
The downside is that the risks involved from a cyber perspective tend to grow exponentially in these scenarios; when controlling your car on the freeway, performing remote surgery or providing power to cities, cyberattacks can literally become a matter of life or death.
On this webinar replay, Threatpost’s Tara Seals is joined by Nokia Threat Intelligence Lab’s Kevin Mcnamee, iboss’ Paul Martini and Sectigo’s Alan Grau to talk about how IoT security will change in the era of faster networks. The discussion covers emerging real-world threats and practical strategies for locking down IoT footprints in 5G-enabled enterprise environments.
Mcnamee presents research that Nokia carried out on IoT botnets and what takeaways we have as we move to 5G, while Martini discusses top IoT attack vectors and security issues, and the potential damage that can come from attacks. Grau concludes the presentations with expert advice on best practices for securing your IoT footprint.
And finally, a Q&A covers the 5G rollout timeline, the importance of adding security to IoT devices during the design phase, carrier network security, how attackers can target specific classes of device and more.
Please see the YouTube replay of the webinar, below, followed by a lightly edited transcript of the event.
Event Transcript:
Tara Seals: Hello everyone, and thank you for attending today’s Threatpost webinar, entitled The Internet of Things: Security Challenges in a 5G Era. I’m Tara Seals, senior editor at Threatpost, and I’ll be your moderator today. I’m excited to welcome our panelists and thought leaders who will give us a comprehensive dive into how security for IoT is changing in a 5G world, along with some best practices for securing IoT in general as these devices continue to proliferate.
Today we’re going to hear from Kevin McNamee who is the head of the Nokia Threat Intelligence Lab, also Paul Martini who is CEO and co-founder at iboss, and Alan Grau, who is vice president of IoT and Embedded Solutions at Sectigo.
Kevin’s going to talk about some research Nokia had carried out on IoT botnets and what takeaways we have as we move into the 5G world. Paul is going to pick up the mantle there and talk about some top IoT attack vectors and security issues and some of the potential damage that can come from attacks like that. And then Alan’s going to round it out with some best practices for securing your IoT footprint.
And with that, I am going to turn it over to Kevin. Kevin, welcome.
Kevin McNamee: Perfect. Nokia has been monitoring malware activity in mobile networks for quite some time. We produce these annual threat reports that summarize what we’ve been seeing. As I said, we collect data from mobile networks around the globe and we’re looking for things like malware, command and control traffic, exploit attempts, DDoS attacks, scanning activity and just general hacking activity. And we’ve been doing this for a number of years, and our most recent report which came out at the very end of 2018, we noticed a couple of things with respect to IoT botnet activity. Okay.
First of all, 78 percent of the actual malware activity we detected were actually due to these IoT bots. You’ll see in a minute when I show you what these bots do, why that is, why they’re so active in the network. Of those, 35 percent of them were actually from variants of the Mirai botnet that came in 2016. And this bot, the source code was released in 2016 and it has been used by hackers to create new varieties of IoT bots since then. And I think that in itself is responsible for the increase in activity that we’ve seen there.
When we look at devices in general, we monitor smartphones, we monitor laptops, tablets, the whole thing. When we look at the infected devices, we now find in the 2018 report 16 percent of the devices that we flagged as being infected with malware of some sort were actually IoT devices. And that’s a very large jump from what we’d seen in previous years.
Before I jump into some of the statistics we’ve got, I’ll just go over the typical IoT botnet operation. And this is based on the original Mirai architecture and it’s been extended by other malware developers over the past couple of years, past two or three year to sort of be, improve it to evolve and create new bots as we go along.
The first thing is an IoT bot. The botnet nodes, they actually spend most of their time scanning the network looking for other victims. That’s their primary, the primary thing that they do. And because of that these botnets naturally increase in size over time. Eventually once they’ve covered all the devices available, again, the botnet sizes are sort of self-limiting. And that’s a thing to bear in mind when we start talking about the 5G thing. Because in the future with 5G, the number of IoT devices is going to increase exponentially and so the size of these potential botnets is going to be quite, quite incredible. That’s one thing to bear in mind.
When an IoT bot finds a new victim, it responds back to its command-and-control server. And then they go ahead and infect that new device that’s been detected. And that device will then become a member of the bot. And the botnet gets larger and it continues to scan. One of the key things here is that in order to be infected, the device has to be visible from the internet, visible from the existing botnet members. That’s another key thing to bear in mind.
Now, once the botnet’s been established, then the bot master, he will, it can either rent it out or he can do what he wants, but typically it’s used for various things. One of the things that Mirai was used for back in 2016 was DDoS attacks, so it attacked, Brian Krebs’ website was brought down. There was nine DNS attack that shut down the internet in North America for almost a whole day. These were fairly significant. The size of these DDoS attacks is going to get larger.
Now, since then have been more modern bots, new varieties, and they’ll do things like, they’ll get into Bitcoin mining, they’ll get into identity theft. There’s a whole, a new series of use cases for these particular botnets that’s become available. Just to show you sort of the botnet, the increase in this botnet activity. Back in 2015, you see we got some, a little bit of IoT botnet activity here. And then all of a sudden in the end of 2016 the original Mirai botnet comes out. In 2017, we get IoT bots based on that basic Mirai architecture that start to come out. And finally, you get it in 2018, you’ve got 78 percent of the malware detection activity coming from these bots.
One of the things I’d like to make as a main takeaway here is that because of the nature of the way that these bots spread, if you’ve got a vulnerable IoT device and it’s visible from the internet, then that device is going to be infected literally in a matter of minutes. That’s just the way these things work. That’s one of the main takeaways there. So bear that in mind, vulnerable and invisible.
This is just a screenshot of what one of these bots looks like from our monitoring system. To give you an idea of the botnet evolution, you had … This is a chart that explains what was going on in 2018. You can see the variety of different IoT bots that are coming on there. Some of these are used for … they’re used for peer-to-peer command-and-control systems. Some of them are used, for example, destructive cyberattacks and DDoS activity. This one here, DoubleDoor, can actually break in through residential firewalls into a residence and infect IoT devices within the residence. You’ve got a variety. So I won’t go into the details there. It’s available in the slide. And if you want more details of any of this, you can pick up our threat report, and they’re all explained in great detail.
The message here is that these bots are getting more varieties of them and more attack vectors and also more sort of uses cases, more purposes that they’re used for.
Okay. So how do we tie this in with 5G? Bear in mind, there are not many 5G networks currently out there, so most of the information you’ve seen so far comes from existing 4G mobile networks. Going to 5G, 5G does introduce some new security features of great value. I mean first of all, on the pro side, the control plane in 5G is strongly authenticated and encrypted. This means that the actual core of the 5G network is going to be less vulnerable to attack, and that’s a really good thing.
The other thing is that 5G introduces the slicing capability, which enables you to create network segments that are completely separate from each other, and one segment can’t be attacked from another. That is a really good thing too. This means that if you’ve got a segment that’s dedicated to electronic banking, then the segment that’s dedicated to mobile phones can’t attack that particular segment. They’re not visible to each other. They’re physically separate. And from a security perspective of course that’s really good.
However, on the con side, more IoT devices means bigger botnets. As I said before, the Mirai type varieties were self-limiting in terms of the size they could get. Once you get up to a few hundred thousand devices, you’d sort of run out of your available cast of characters for your botnet. But with millions or billions of IoT devices out there, these botnets can get much, much bigger, which means they’re much more dangerous. Also, with the enhanced bandwidth, Tara mentioned the phenomenal bandwidth increased with 5G, it means that this DDoS capability is now much, much, much larger in terms of its ability to do damage to the network.
Another aspect is that, and this is the visibility aspect, within a lot of the mobile networks today the use carry a great net and so the actual mobile devices are not visible from the internet. They can’t attack them from the outside. But with 5G and also the move to IPv6 addressing, it could create the situation where the IoT devices out there, unprotected, no firewalls in front of them may be much more visible and therefore much more vulnerable to attack. Remember, I’ve said if the device is vulnerable and is visible, it is going to be attacked.
I think finally, the slicing thing, although it provides a really good security aspect up here by providing the network segmentation, it can provide a focus for attack. So for example, if I’m an attacker and I know this particular slice is hosting that banking application or that medical application, I can focus my attacks on this.
I basically say to summarize, and I think a little bit later on Alan’s going to be talking about best practices so I’m not going to get in much details here, but to summarize: Securely managed, confident secure communication, you’ve got to monitor, you got to watch this network for this malware activity. If you don’t look and see what’s happening, you’ll never know that it’s going on until it’s too late.
My takeaway here is the network security team, the person managing this 5G network, must be able to detect rogue IoT devices and take automatic action to get them off the network, to quarantine them, to get them taken care of. So that’s my section. And I think now what I’d like to do is I’d like to pass it over to Paul who’s going to talk a little bit more about attack vectors.
Paul Martini: Thanks Kevin. So, given the pervasiveness of 5G connectivity, which actually in some cases even exceeding 10 gigabit per second as we move forward into the future, the amount of attack vectors are increasing by the day. So one of the things I want to cover specifically around vulnerabilities, we work a lot with our partners like FireEye who do a lot of research and remediation around industrial control systems, as well as IoT, and actually a lot of the findings throughout a lot of the data that we’re seeing in the cloud as we process transactions, DNS queries, data requests, including HTTP and advanced protocols, always by malware and botnets to infiltrate IoT devices, one of the things that are fundamental to these changes is the fact that the network perimeter is really changing and evolving.
Traditionally, and Kevin mentioned this in the prior slides, is that you create a castle-and-moat mentality, you have access to all of your servers, all of the data that gets generated from these servers traverses security stacks, firewalls, proxies and things like that. But as you move into the future, the notion of a fixed perimeter goes away, meaning that devices are everywhere, and actually IoT devices in particular are everywhere, because they’re connected to 5G networks. So when that comes into play, one of the key fundamental principles of threat actors is scanning for IoT devices or vulnerabilities within those devices in order to discover new potentials and new opportunities. But when these devices are not sitting within controlled physical environments, that becomes really, really challenging.
So you can see that this eroded perimeter leads to the inability to scan for botnet callbacks and command-and-control. But also, when you think of different types of devices, cameras, utilities, they’re all connected wirelessly through there, also potentially open to breaches through lack of patches or other mechanisms. With that you combine encrypted traffic, which is exceeding now in our last measurements, over 90 percent of the traffic is HTTPS or encrypted, and typically the vast volume of traffic if you think about the future will likely hit near 100 percent encrypted point-to-point communication, which is a really good thing for both communication over the internet but can have it the flip side where botnet communications and data exfiltration specifically from IoT devices will occur over encrypted channels. So it’s very hard to detect these callbacks and things of that nature when the traffic is masked within encrypted traffic.
The combination of encrypted traffic as well as increasing exponential bandwidth speeds not only increases the surface area, but it also makes it a very, a big path to hijack or exfiltrate data. Through the research and a lot of different engagements really, if you look at the breakdown in terms of the risk, a big portion of the risk that were found were actually categorized as high or critical. And really when you think about when you’re thinking about high or critical, that actually means that it has the ability for an actor to gain access to a system as well as take over that system and use that system to cause either disruption, access information, or exfiltrate data. So high and critical really means impact the organization in a major way.
As you look at the primary three areas that were found, really the largest floods, vulnerabilities and patches, now when you think about IoT, it’s not like Windows or other operating systems that can receive regular updates. They’re embedded devices a lot of times. So even patching and updating them can be very challenging. It’s also more firmware than it is software and so that makes it a lot harder to maintain and upgrade and do patch management.
Twenty-five percent was identity and access management. I’m going to talk about some of the very basic things that were found that literally could lead to critical breaches and then segmentation. In a world where the perimeter’s fixed it’s very easy to isolate one network from another, but in a 5G world where things are connected wirelessly, not only is segmentation important but the ability to have all of the connectivity from all IoT devices run through a security system regardless of its location. We’ll talk a little bit more about that.
But here you can see a list of all the different risk categories, the top three which as I just showed being vulnerability, patch management and updates, identity and access management, as well as segmentation. And then it really starts to drop off with a lot of other areas as far as insecure services being enabled, so software enabled that really shouldn’t be running to begin with, as well as other best practices that follow SOC 1, SOC 2 compliance, as well as ISO compliance.
So going back to these top three categories I want to focus on these, because really if you think about maintaining and controlling these three areas, you’re really covering a lot of the core surface error for thread actors to hijack data and take over systems. But really, as we think about the patches and vulnerabilities, again, very difficult to update IoT devices, but really these are known vulnerabilities in IoT that allow threat actors to get into the devices and then use those devices to access other servers. And that’s pretty common. IoT, it’s not just the hijacking of the device but it’s also using that device as a vehicle to access laptops, servers, and other things that contain critical information, as well as using them to hop data through that IoT device itself.
With identity access management, the second most common category, a lot of the issues were related to just really best practices and the way passwords were handled. And then the network segmentation and segregation, as you think about these wireless devices, just the mixing of these devices with critical servers, remember these actors are using them for horizontal exfiltration, hopping through devices to get to servers.
But as we go back to the number one core issue was vulnerabilities and patches, and of course, again, very hard to update these IoT devices. But really in a 5G era, it’s going to be exponentially harder to control and secure these devices because the devices are not necessarily located within your controlled network. So thinking about how to connect these devices to services that are either SaaS or cloud for example, not only are these services always up-to-date but they basically cover the device inside and outside of a traditional network perimeter.
Looking at some of the areas for risk around vulnerability, patches and updates, what we found ranged from infrequent updates. That’s very common, probably the most common in terms of not patching the devices, not upgrading them. You install them. Some are hard to get to as well. So being able to update those are really important. But we find things like outdated firmware and software. There was also, just looking at old operating systems that might be running, we found scenarios where they might be an embedded version of Windows for example or an XP, a sort of a kiosk environment that just isn’t getting patched anymore to end of life. A lot of them were known vulnerabilities.
We’re not talking about some sort of threat that just came out. These were threats or vulnerabilities that were around for a while. And the threat actors know that IoTs are a very good spot and this is why the search for them to really attack devices because of old operating systems.
As you think about risk mitigation in that area, you really have to develop a strategy, just putting up devices especially in IoT and now in a 5G era without a plan is definitely dangerous. There’s lots of guidelines around that for compliance including some from NIST. There’s NIST documents around that area as well. And then as you think about just planning for staff, it might seem putting up cameras or some sort of remote entry sensors are a good idea, but without the staff to do the patches and do things like that it’s going to really create a gap and a hole that allows threat actors to get into more sensitive information and maybe even gain access to offices and things of that nature.
And then, as you think about other areas and the lack of patching, filtering and traffic control become really critical, monitoring of traffic Kevin mentioned is really critical, as well as ensuring that there’s up-to-date rules and rule sets as these devices communicate, because even though the IoT software may be out-of-date, it doesn’t mean that the rule sets that are governing their communication should be. So you really want to look at scenarios where you can connect these devices, possibly to a SaaS or cloud security system that is always up-to-date, find that to be a really good strategy especially with overburdened staff where they don’t have the time to patch or do upgrades potentially to allow third-party services to do those patches. You’ll find a lot of that with cloud security for connectivity but also within SaaS platforms like Office 365 and things of that nature where you can extend your IT staff with the help of other vendors.
From an identity and access management really the core bulk here is look if you can get multi-factor authentication, that’s actually obviously powerful. Both IoT many times that’s really not an option. But if there’s access to, administrative access to these IoT devices, things like cameras, remember, they can be accessed now with 5G from a 5G wireless network which isn’t even the organization’s Wi-Fi network. But if you look at this, the list of password mishaps, it’s pretty vast. Anything from weak passwords, passwords that are never changed, sharing passwords, and also we’ve seen scenarios where they’re actually the default passwords. They’re never changed to begin with. That’s still very common.
So you really want to do something as basic as a strong password, which really goes a long way, as well as not using administrative passwords for access to IoT devices and things of that nature. Avoid keeping copies of passwords anywhere. And that goes across the board and it’s pretty common, but it still happens to be a big vector, especially in the 5G era.
And then if they do support multi-factor, that’s always the preferred choice. It does provide an exponential amount of security even if a password gets compromised, they’ll have to have additional token or additional device to gain access. And then avoid even from a username perspective, if you have the ability to change a username, change it from the default admin or administrator as these botnets scan for IoT devices, they’re using dictionaries and they’re using very common usernames to get across to these IoT devices.
And then lastly from a segmentation perspective, keeping the network separate from your core network from IoT devices is always good. I mean a 5G world when these devices are connected through wireless networks, using cloud security services is a good idea. You can connect these devices to the security service, which goes beyond the traditional network perimeter. It’s a really good way to segregate the traffic and ensure that the rules are always up-to-date and you’re running the latest without the need for patching and upgrading and doing things of that nature.
So with that, I’m going to pass it over to Alan who will continue on with his presentation.
Alan Grau: All right. Thanks Paul. As Paul said, my name is Alan Grau, and I’m the vice president of IoT and Embedded Systems for Sectigo. A lot of what I’m looking at and thinking about and the solutions we’re focused on are really about security at the IoT device level. And so as I look at it, a lot of my focus is much more device-focused than network-focused. So I may have a little different perspective on a few of these things, but I think it all ties in together quite nicely. The main thing I’ll be talking about are just best practices for IoT security, particularly as it relates to 5G.
As we look at IoT device security, there really are a number of challenges. Again, as I said, I really think security has to start with the device. I mean clearly network security is critical, ensuring that you’ve got all the right infrastructure in place and security of the network level is an important part of it. But ensuring that the devices themselves are secured is really a fundamental piece of the overall equation. I’ve had conversations with people that are saying things like, “Well, I’m building an IoT light bulb. I’ve got connected light bulb and, yeah, I don’t want it to get hacked. But really what’s the consequence? Is it that big of an impact if my device is compromised?” And the reality is that it is.
Paul talked a little bit about how attackers will move horizontally once they compromise a device. And we’ve seen instances where a hacker has compromised something like an IoT light bulb. From that they’ve been able to steal Wi-Fi passwords, gain access to the broader network, and that’s the actual initial infiltration point to a much broader attack. I mean, if we look all the way back to the target data breach, that was an attack that came in through an HVAC system, essentially connected IoT device that was compromised. So it really is critical to ensure that the device is secured.
But as we look at IoT devices, in many cases these are specialized embedded devices. They’re not easily updated. They’re running specialized OS, real-time operating system perhaps Android or often times in some cases Linux and the larger devices Windows, but in many cases it’s an embedded real-time operating systems like Integrity, VxWorks, or one of the dozen or so other real-time operating systems. And these solutions have limited resources. They aren’t easily updated. And while you’ve got the same security challenges for these devices, you need specialized systems to protect them. The existing enterprise software for security won’t run on these devices.
We’ve talked quite a bit about how widely deployed these devices are and how that’s changing with 5G or at least increasing dramatically with 5G. We also have the challenge that these devices are deployed in the field. So, in addition to having network-based attacks, you have to be concerned about physical attacks. A hacker could come up, steal a device in many cases, take it home, crack it open, pull the flash out or access the device, and gather data and steal secrets from the device that way. So there are new attack vectors that we need to be worried about.
And they’re also built using new technology. Security vulnerabilities, there are many different types of security vulnerabilities, but one of the classes of security vulnerabilities are just the result of programming flaws or bugs, things like buffer overflow attacks because the system wasn’t implemented properly, allowing that type of attack. They’re not the battle-hardened solutions that we see in other areas and so it’ll take time to really flush out all those vulnerabilities and harden the devices.
As was mentioned during the intro by Tara, these devices are performing critical tasks, so the security requirements are even harder … higher than with traditional IT devices. If I lose personal information, my credit card is stolen, that’s an inconvenience that may cost me a little bit of money. But if my medical device, if my connected car malfunctions, whether it’s due to a cyberattack or other cause, that can actually cause loss of life. So the security requirements are really critical here.
As we look at the approaches for IoT security, especially at the device level, the challenges really are similar to what we’re seeing anyplace else. They’re the same as we see in IT networks and so on. We need strong authentication. Static credentials just won’t cut it anymore. Paul talked about the botnets that are out searching for known account names, known passwords. In other cases there have been devices that are produced with SSH keys, but the same SSH key in many, many devices. Well, those often end up getting discovered. That information gets put back into a botnet and the botnet can go out and use what seemed like strong credentials in a SSH key, but it’s been discovered and it’s in thousands of devices, making it vulnerable to attack. So strong authentication is critical.
Device integrity is another important piece, ensuring that you’ve got secure boot enabled in the device so that you know your device is always running your code and having attack detection built into the device. And this becomes a challenge in lower-end devices. If you’re talking about a sensor, a connected light bulb, a wearable device, you can’t run traditional Windows-based security solutions, so you need something that’s specialized and will scale to these devices.
Another critical issue obviously is data security and data protection. This really involves two pieces. One is secure key storage. Whether or not you’ve got hardware device built into your IoT device for storing the key securely or you’re doing it in software, you need some method of ensuring that the keys are stored securely. And then again that you’re securing data both at rest and in motion. Obviously with 5G you’ve got some built-in capabilities around securing communication, but you still have to secure the data on the device and with regulations like GDPR and other strong regulations this is even more critical.
And then finally, visibility and management. This is some of the things again that we talked about already in terms of making sure you have patches to your devices, making sure that their firmware is updated, and doing so in an automated fashion.
So how do we implement these things? Well again, we’re looking at resource constrained devices, so you do need a purpose-built solution for an IoT device that’s tailored to these use cases. It’s also critical you design in security. Again IoT devices are new devices. These are things that are being designed that are using in many cases unique and new resource constrained hardware, new software that’s being developed, and the security capabilities require things as I said before like secure key storage which needs to be built in at a hardware level if it can be. So that requires security to be addressed very early in the design cycle.
One of the other considerations obviously is the build-versus-buy consideration. Since these devices do require specialized security solutions, you’ve got to figure out the best way to get that put into place. And these solutions are complex. Engineering teams typically are very busy. They have a lot of work to do to build whatever it is that their company’s good at building, and doing that themselves can often be cumbersome and error-prone.
And then finally, as you look at IoT device security, there are a number of hardware based solutions that have been created and are being developed by chip manufacturers to enable security in the device, things like secure elements, TPM chips, and TrustZone which provide the hardware foundation for security for IoT devices. Then on top of that there are software-based solutions for secure updates, secure boot, data protection and so on that can be added.
If we look at how this all comes together in 5G, well first off, an IoT device is still an IoT device and still a device that needs to be secured. In many ways the basic security fundamentals are the same. Every IoT device must be secured. You need to ensure that you’ve got secure key storage, secure data management, the ability to update the device in the field, ideally a way to automate that, strong credentials. We see PKI is an important part of security for IoT devices so that you can authenticate the device, and as devices are talking to each other, they can authenticate each other so that they know they’re talking to someone that they should be. They aren’t talking to a command and control center for some IoT botnet, but they’re actually talking to the systems they were designed to talk to.
The broad attack surface is something that Kevin talked about quite a bit in his presentation with IoT. Just the vast number of devices that are being deployed and will continue to be deployed with 5G and the connectivity of all of those devices creates really a very, very broad attack surface. One of the areas that really can come into play is with botnet conscription. The ability to conscript devices into a botnet is something that as devices are deployed with weak credentials and weak security, and again, we’re continuing to see new devices deployed with those weak … in many cases with weak security and weak credentials, they’re going to be conscripted into botnets and the size of those botnets is growing, leading to just more and more damaging attacks.
And then finally, the other consideration for 5G is while 5G’s a very exciting new technology, it’s creating the opportunity to implement solutions that weren’t possible before, it’s also going to create new types of devices with new vulnerabilities. Many of these devices aren’t battle-hardened, they’re immature, and it’ll just take a lot of time for security vulnerabilities to be fixed, found and fixed in these devices which is all the more reason it’s critical that security be addressed in the design of the devices that security’s built in, that security testing is part of the process, and that we really put security high on the priority list as we’re looking at designing new devices.
I know we were going to take a little time for Q&A so I’m going to pass this back to Tara so we can take questions and answer any questions that anyone has.
Questions and Answers
Tara Seals: Thank you so much Alan, and let me just pull up my screen here. Okay, great. So yes, so we wanted to take a few moments for Q&A. Let me just start off with the first one that was submitted here which is the question about IPv6 addresses. They wanted to know, would hard-to-guess IPv6 addresses limit the scan efficiency for the bad guys looking for vulnerable open devices?
Kevin McNamee: Certainly. I think the fact that the IPv6 address space is so huge, it will make it more difficult to scan. But you can focus on specific subsets of that address space. I think the fact that the device is visible itself is a bigger threat than the fact that it’s visible in a large, a very large sort of pool that might be difficult to scan.
Alan Grau: I think the other part of that is as these IoT botnets proliferate, they can break the address space down and each botnet or each node in the botnet can scan a subset. So once a botnet gets a foothold and starts to gain a number of devices as we’ve seen some very large botnets, that that will allow scanning to proceed pretty quickly despite the larger address space.
TS: Thanks Kevin and Alan. And then, another question is about 5G in general. There’s a lot of hype obviously arounds this technology. Some of the audience members wanted to know are we dealing with kind of a pipe dream here or are 5G networks with all of the attributes that we’ve been talking about, is that realistic anytime soon? What’s the timeline on 5G roll out?
Paul Martini: Well, a lot of the carriers are actually trialing the 5G in the RAN at the moment. That’s stuff that’s been tested today. 5G in the core people are saying it’s anywhere from one to two years away. So it is real and it’s certainly coming. As I said, we are actually rolling out networks in the RAN today.
TS: And the other question is too, is that even if 5G is not widely commercially deployed right now, it does seem that the security challenge is rather broad reaching. So probably something to start thinking about if you have a business that you will be looking to implement this kind of wireless technology in the future, correct?
AG: No, I would completely agree with that. I think that the security challenges are largely independent of 5G. I mean 5G with the scale that it provides does create larger opportunities for security breaches and for botnets to do greater damage due to their or scale, but the base issues still are there.
AG: I think the other point to make with this is that design and development of new devices, especially if you really are thinking carefully about security and trying to build in new devices with secure elements for secure key storage on the device and so on, it really does take time so it’s never too soon to start thinking about adding security to these devices.
TS: Another question has to do with actually the IoT device vendors themselves. We’ve seen this in the 4G era as well where you don’t necessarily have security built-in in the design phase as you say. So you end up with a case where you have things that need to be recalled or that need firmware upgrades and things like that. Are these recalls going to become more common as we go forward do you think? What’s going to happen on the security front there?
AG: This is Alan. In some cases we’ve already seen device recalls. Particularly in automotive there have been security vulnerabilities that a number of automotive manufacturers have had to do large-scale recalls to address. One of the ways to mitigate this is by building remote secure firmware updates into the devices themselves that allows obviously over-the-air update so you don’t actually have to pull the device back in to whether it’s the auto dealership or back to the manufacturer to update the device. So really there are two parts to it.
AG: But yeah, I do see this as being an ongoing problem and something that will continue to be a growing problem. And just depending upon the nature and the cost of the device and the responsiveness of the manufacturer, we’ve certainly seen cases where manufacturers have just ignored security vulnerabilities and not addressed them, but their ability to do that and remain competitive is going to be more and more difficult, so I do expect this to be something we see more of as we go forward.
PM: And this is Paul as well. As you think, there’s cases of recalls that have occurred recently. But if you think about IoT devices, sometimes they’re installed in areas that are very difficult to reach, especially when it comes to cameras and things of that nature. So even though there’s a recall for a vulnerability, it doesn’t necessarily mean that you can get all the devices back quickly and back to the manufacturer.
PM: We suspect that at the minimum as the manufacturers become more sophisticated at the minimum they are producing patches and updates because the understanding that these could cause severe damage and the need to come up with a strategy as you deploy IoT devices especially in hard to reach places that allow access in order to perform those updates is going to be required. I think a baked in strategy that involves update plan and access to updates is definitely important before rolling out any sort of IoT strategy.
KM: Yeah, Kevin here. It can also be mitigated somewhat … by using an IoT device management system that will sort of sit on top and manage the IoT devices, ensure that they’re updated. That’s a solution that the IoT owners, the people who own these networks of IoT devices, can undertake themselves. That’s another possibility.
TS: Great. We had a question on the carrier network side of things. Kevin, in your presentation you had mentioned that there are several DDoS attack vectors. This person would like to know what recommendations would you provide to the carriers themselves in order to mitigate some of the attacks filtering down to end-users.
KM: Okay. With respect to DDoS itself … what we recommend at Nokia is that if you can detect the devices that are part of the botnet and basically dismantle the botnet before it does the DDoS attack, that’s the most effective way to mitigate that threat. Short of that, there are a number of DDoS protection systems out there that you can get from a number of different vendors to help alleviate that. A lot of these weren’t really that effective during the Mirai outbreak. It sort of broke a lot of these DDoS-protection systems. Early detection and mitigation I think is the best way to go there.
PM: And this is Paul. We work very closely with telcos like Verizon which are doing a big push in 5G. Actually the notion of security being baked into the wire, baked into connectivity is a big initiative across the telcos like Verizon. So when you think about, as Kevin said, there’s the DDoS component which you’re providing big connections and big pipes to IoT devices so you want to be able to absorb that as close to the carrier as possible.
PM: Then the other part of it is, if we can bake in, and this is what they’re pushing towards, the actual rules, the security rules, intrusion prevention signatures and botnet signatures into the actual 5G connectivity itself, that would ensure that no matter where the devices are located, they always have secure connections at all times.
PM: I mentioned a lot around this, around cloud security in general. It’s really the same concept which is the devices are connected in this case wirelessly to networks you don’t control. So being able to apply security in a consistent way that’s always up-to-date becomes really critical and actually it’s one of the top areas where we see the breaches occurring.
TS: Okay. Great. We have another question in terms of security tools from a system perspective. What about the role of artificial intelligence and automated vulnerability hunting and that sort of thing? Is this something that is emerging in defense tools as we go forward to 5G rollouts?
PM: This is Paul. Yeah, actually there have been huge advancements. AI plays a critical role in a few ways. One is in the transfer of malicious content. So if you think about malware today using signature based techniques which they change almost immediately on a file to file basis where you cannot detect the file as malware using a traditional pattern, using AI in that area as well as signature-based tools. The same goes for the analytics component, AI around botnets, patterns and callbacks, and things of that nature. And then lastly in terms of the rules the get applied, just anomalous behaviors in terms of larger volumes than normal as these IoT devices get auto profiled. But in order to scale and apply security in a world where everything’s connected, AI is actually critical. There’s no amount of human horsepower that can actually condense and compile the needed information into meaningful results.
KM: Yeah, that’s an excellent point. At Nokia, we actually got our Bell Labs people working on AI to handle that IoT device-profiling so that we can automatically tell when the device misbehaves, we can flag that and we know that right away. So that that’s the sort of a thing that we’re actively working on at the moment and I think it’s very important.
TS: Okay guys. Well, we only have a few minutes left so I wanted to give you each an opportunity to have a wrap-up statement, the biggest takeaway from our discussion today. Kevin, if you want to start, and maybe Paul and then Alan to wrap it up.
KM: Sure. I think my main takeaways were the fact that if the device is visible and it’s vulnerable, then it’s going to be hacked very quickly. So the key thing from my focus and security is make sure it’s not vulnerable, which means the secure patching and management, and then make sure you can protect it from visibility using network segmentation or whatever, that is a real plus too. So I think that’s my takeaway from this.
PM: And the main takeaway, this is Paul, is that the world … The perimeter’s changed. With the 5G world it’s all wireless, so the devices are connected from anywhere and they have a volume of data that can be transferred between these devices like never before. So that means that when you think about data hijacking, records and things of that nature, they can be used as vehicles to access critical servers and critical data.
PM: So really, thinking holistically about the security challenge in a different way which is not focused on protecting of physical four walls or physical servers and things of that nature to a world where things are not only IoT and of all types, but also connected from anywhere with large connections. So being able to apply the needed network security elements to that connectivity and in a way that applies to all the devices consistently wherever they’re located. And then ensuring that these smart devices and smart IoT receive continuous patches and the things that are needed to prevent hijacking in the future is going to be very critical coming in the future here.
AG: I think Kevin was saying that if the device is visible and vulnerable, then it’s going to be attacked. I completely agree with that. And Paul was saying that the perimeter has changed. I think in many cases there really is the concept of a perimeter really doesn’t even exist anymore. The devices are out in the field. So they are going to be visible, if not through just your standard IP address searching, they are physically accessible to attackers.
AG: With those changes, it really is critical that we don’t rely on the perimeter and that we build security into the device, that we have strong identification of the device, strong IDs in the device, strong secure boot solutions in the device, that we really ensure that the device is hardened, protected from being attacked, and again that we have those strong identities so that we can ensure that the device is really who we think it is and that when it’s talking to another device or the cloud service that you can do the mutual authentication required. The fundamentals of device security are just growing more and more important as we move forward.
TS: Okay, great. Okay guys. Well, I think we’re going to have to leave it here. I would like to thank all of our panelists. You guys were great. Kevin, Paul, Alan, I really appreciate your time today. Thank you for joining us.
TS: If anybody had questions that they did not get answered or that they think about later that they would like to have answered, this is my email address taraseals@threatpost. Please go ahead and feel free to shoot me a line any time.











