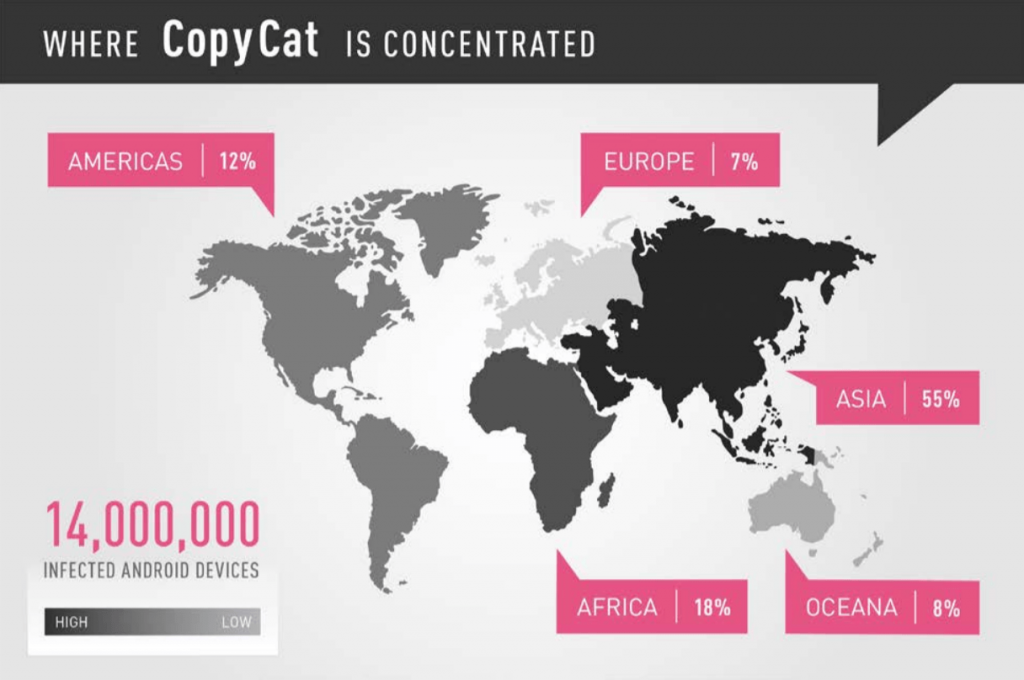
A family of Android malware was so successful that at its peak, over the course of two months last year, it infected 14 million devices and rooted more than half of them, roughly eight million devices.
Researchers said early Tuesday the strain of malware, dubbed CopyCat, helped its authors earn $1.5 million – primarily through ad fraud – from April to May 2016.
Researchers with Check Point’s Mobile Research Team, who found the malware in March this year, claim CopyCat mostly infected Android users in Southeast Asia, but that upwards to 280,000 U.S. Android users were also infected. According researchers, Asia accounted for 55 percent of CopyCat infections. Africa, at 18 percent, accounted for the second highest number of infected devices.
The malware never made it to Google’s Play marketplace, but did spread via popular apps, which were repackaged with CopyCat and available for download on third-party app stores.
The malware lingers until the infected device is restarted; once that happens, it downloads a series of exploits from an Amazon S3 bucket and attempts to root the device.
“If successful, CopyCat installs another component to the device’s system directory, an activity which requires root permissions, and establishes persistency, making it difficult to remove,” the researchers wrote Thursday.
Once in, the malware targets Zygote, an Android core process that launches apps and if exploited, essentially grants attackers admin privileges.
Triada, an Android Trojan uncovered by Kaspersky Lab, and later by Check Point in 2016, previously used this technique. Kaspersky Lab’s Anton Kivva, a malware analyst with the company, said in June that year Triada was infecting Zygote, obtaining super-user privileges, and using Linux debugging tools to embed a malicious DLL to target mobile browsers.
Researchers at Check Point claim that with the CopyCat malware, attackers have taken a shine to injecting code into the Zygote process to get credit for fraudulently installed apps on the device by swapping out referrer IDs for legitimate apps with their own. The malware also displays fake ads and installs fake apps, two additional methods of generating capital for the attacker.
Researchers were able to get a better idea exactly what attackers were doing to victim’s devices by looking through one of the malware’s command-and-control servers. Daniel Padon, a mobile threat researcher with Check Point told Threatpost Thursday researchers have the data from a C+C going back more than a year. Between April and May 3.8 million of the devices were being served fake ads while 4.4 million other devices were being used to steal credit for installing apps on Google Play, the firm claims.
The bulk of the exploits CopyCat used to root the eight million devices are years old, according to Check Point. Four of them were from 2014, one was even from 2013, suggesting victims either didn’t patch their devices, or patched infrequently.
One of the exploits, Towelroot (CVE-2014-3153) was behind a scourge of auto-rooting malware this time last summer and a wave of Android ransomware attacks in April of that year that targeted outdated systems.
Researchers are unclear who exactly is behind CopyCat but note there are several connections to MobiSummer, an ad network based in China. It’s possible the attackers simply used the network’s code and infrastructure however.
Check Point says Google, which it informed of CopyCat in March – shortly after it discovered the malware – has been able to “quell the campaign” over the past year.
When reached by Threatpost on Thursday a spokesperson for Google said the company has been familiar with CopyCat – malware it says is a variant of a larger, undisclosed malware family its monitored since 2015.
“Each time a new variant appears, we update our detection systems to protect our users. Play Protect secures users from the family, and any apps that may have been infected with CopyCat were not distributed via Play. As always, we appreciate researchers’ efforts to help keep users safe,” Google said.
Google introduced Play Protect, a service that scans previously downloaded apps to ensure they’re safe from malicious components, in May at Google I/O.
Padon told Threatpost the malware demonstrated a number of new techniques, and that as far as he knew, wasn’t connected to another family.
“We didn’t manage to affiliate this malware with any other known family,” Padon said, “It also presents a lot of new techniques which were never seen before. If Google does come up with a name it will be interesting to know.”
CopyCat joins the ranks of other Android malware strains previously discovered by Check Point, like HummingBad and Gooligan. Gooligan was blamed for the breach of 1 million Google accounts this past December. HummingBad, disclosed by the firm last July, reportedly raked in $300,000 a month for its authors via adfraud. Both families of malware installed adware on infected handsets in order to generate revenue.