Brazilian bank customers are being warned of malware dubbed CamuBot that hides in plain sight and presents itself as a required end-user security module provided by a bank.
The malware goes so far as to include bank logos that look and feel as if they’re part of a real security application. In some cases, the malware can also hijack one-time passwords used for biometric authentication.
In a report by IBM X-Force released Tuesday, researchers said CamuBot was first spotted in August 2018 in a targeted attack against business-class banking customers. The name, CamuBot, was given to the malware because it attempts to camouflage itself as bonafide branded security software.
“The malware’s operators are actively using [CamuBot] to target companies and public-sector organizations, mixing social engineering and malware tactics to bypass strong authentication and security controls,” said Limor Kessem, a global executive security advisor with IBM Security, in a technical breakdown of the attacks posted Tuesday.
Distribution of the malware is believed to be highly individualized. “It is very possible that [the threat actors] gather information [on potential targets] from local phone books, search engines or professional social networks to get to people who own a business or would have the business’ bank account credentials,” Kessem wrote.
Once a target is defined, the attackers pose as bank employees via phone calls, and instruct victims to visit a specific URL to verify that their “security module” is up-to-date. The fake verification site will then indicate a fake “required update” for the supposed security software. Next, victims are told to close all running programs, and to download and install the malicious software using the Windows admin profile.
“At this point, a fake application that features the bank’s logos starts downloading. Behind the scenes, CamuBot gets fetched and executed on the victim’s device,” the researcher said. “The name of the file and the URL it is downloaded from change in every attack.”
As the attacker is on the phone with the victim, “a pop-up screen redirects the victim to a phishing site purporting to be their bank’s online banking portal,” Kessem explained. Victims are instructed to log into their account via the fake site maintained by the attacker. Once accomplished, the victim has shared their banking credentials with the attacker.
Outsmarting Biometric Hardware Protections
In some circumstances, such as the presence of biometric authentication or other strong authentication hardware attached to the targeted PC, CamuBot goes the extra mile. “The malware can fetch and install a driver for that device,” researchers said.
To perform this type of authentication end-run, attackers take advantage of the malware’s advanced features. That includes CamuBot creating new firewall and antivirus rules to make sure the malware is a trusted program. Communication is then established with the adversary’s command-and-control via an SSH-based SOCKS proxy. Next, port forwarding is enabled and used “in a two-way tunneling of application ports from the client’s device to the server,” researcher said.
“The tunnel allows attackers to direct their own traffic through the infected machine and use the victim’s IP address when accessing the compromised bank account,” she said.
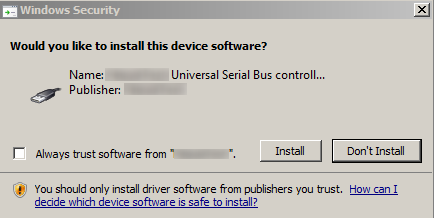 Now, CamuBot asks the victim to install remote access to their USB-connected device.
Now, CamuBot asks the victim to install remote access to their USB-connected device.
“Trusting that they are speaking to a bank representative, the victim may authorize the access, not knowing that by sharing access to the connected device they can allow the attacker to intercept one-time passwords generated for authentication purposes,” Kessem wrote. “If the same remote sharing is authorized by a duped user, they could unknowingly compromise their biometric authentication.”
The CamuBot malware code distinguishes itself from copious banking malware and trojans found targeting Brazil-based financial institutions over the past year. For one, it does not attempt to hide itself as does Brazilian banking malware samples: Trojan-Proxy.PowerShell.Agent.a, Metamorfo, MnuBot and one malware family that used Compiled HTML Help files to deliver a banking trojan.
“CamuBot is more sophisticated than the common remote-overlay type malware used in Brazil in its M. O. (modus operandi) and fraud tactics. Instead of simplistic fake screens and a remote access tool, CamuBot tactics resemble those used by Eastern European-made malware,” she said.
Kessem said CamuBot is most similar to Europe-based TrickBot, Dridex and QakBot, which target business banking and leverage social engineering for account and device takeover.










