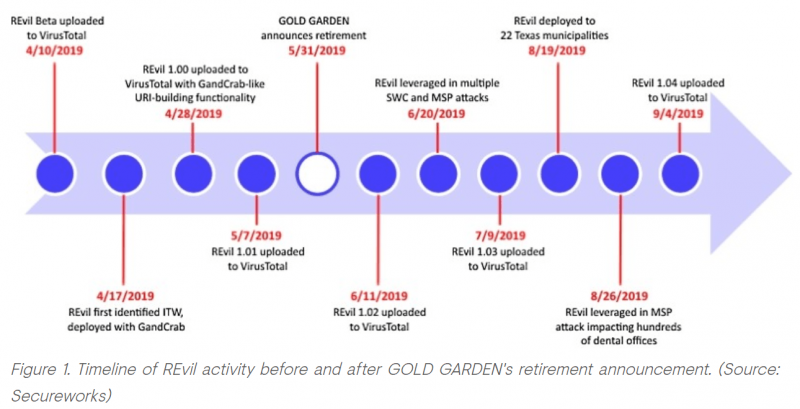
The malware that hit 22 Texas municipalities and various dentist offices around the country recently is likely the work of the crew behind the GandCrab ransomware – indicating that the group didn’t really retire after all.
In late May, the GandCrab operators said they decided to ride off into the sunset with the earnings from their ransomware-as-a-service efforts, which had netted them at least $2 billion since January 2018. But researchers from Secureworks Counter Threat Unit (CTU) researchers said that the group, which it calls Gold Garden, merely moved onto a different ransomware, known as Sodinokibi or REvil.
CTU had been tracking REvil as the work of separate authors, which they called Gold Southfield.
“CTU analysis and tracking of REvil samples suggest that the ransomware was in development and testing between April 10 and May 7 and was not intended for public release,” explained the researchers in an analysis on Tuesday. “Following the release of version 1.01 on May 7, the REvil developers…began pushing a new release of the ransomware at the beginning of each month. This cadence and the ransomware’s capabilities indicate a structured development process by dedicated and experienced malware authors.”
REvil activity spiked after the GandCrab retirement announcement, they said, with campaigns using email spam and remote desktop exploit attacks regularly cropping up – this, according to researchers, indicated that REvil was officially launched.
According to a technical analysis of REvil, CTU researchers found that the string decoding functions employed by REvil and GandCrab are nearly identical.
“Because malware authors typically implement custom encoding/decoding logic in their malware, the code can be used as a fingerprint to identify other samples associated with the malware family,” the researchers wrote. “When analyzing REvil, CTU researchers identified and extracted a portion of the opcodes associated with its string decoding function. When searching VirusTotal for samples containing this opcode pattern, 286 unique samples were identified. Further analysis of all 286 samples were confirmed to be either GandCrab or REvil.”
The two ransomwares also share similar URL building logic, according to the technical breakdown – indicating that code originally created for GandCrab was repurposed in REvil. The researchers said that for the logic to be reproduced inadvertently is outside the realm of possibility, and that the attacker would have needed to reverse-engineer a GandCrab sample to match the logic so closely.
“REvil 1.00 implements URL building functionality that produces the same command-and-control (C2) URL pattern as GandCrab,” according to the researchers. “The C2 URLs for both families consist of two URI subpaths followed by a randomly generated resource name and an extension. The subpath names and extension are retrieved from…hard-coded values.”
Another finding that shows that REvil was likely meant to be GandCrab version 6.0 (the last observed version is 5.2).
For instance, the REvil Beta sample includes the d:\code\csrc\!1\new_a\gcfin\bin\debug\rwenc_exe_x86_debug.pdb debug path.
“gcfin is the malware author’s name for the development project, and in context with other evidence appears to refer to ‘GandCrab Final,'” wrote the researchers. “Similarly, the discovered REvil file decryptor executable specifies the D:\\gc6\\core\\src\\common\\debug.c debug path. The reference to gc6 in the debug path could be a reference to GandCrab 6, which suggests that REvil was originally intended as GandCrab version 6.”
Meanwhile, the REvil sample analyzed by CTU includes a version number with a hard-coded value of 1536, which converts to hexadecimal is 0x600 and indicates version 6.00.
“This version does not align with REvil’s incremental numbering pattern as the next release is version 1.00, but it would align with the GandCrab numbering pattern,” researchers said.
GandCrab burst on the scene in 2018 and quickly became a top threat worldwide.
“GandCrab’s ‘ransomware-as-a-service model’ proved to be a highly lucrative endeavor for Gold Garden, so it is unlikely that the threat actors abandoned all malicious activity,” concluded CTU researchers. “Characteristics of REvil that appear to be operational security mistakes by the malware authors enabled CTU researchers to technically link the REvil and GandCrab ransomware families.”
The sentiment that cybercriminals are unlikely to ditch malware development even if they go quiet was recently echoed on the Threatpost Podcast. The infamous Emotet trojan has returned after a four-month hiatus, indicating that its authors likely just went on vacation.
“A lot of our threat actors … have a culture that really dictates a lot of vacation time,” Sherrod deGrippo told Threatpost’s Lindsey O’Donnell in a recent video. “We also see that they make a lot of money. And so if you have a lot of money and a flexible schedule, a summer vacation for a couple months is nice thing to have on the docket.”
Interested in the role of artificial intelligence in cybersecurity, for both offense and defense? Don’t miss our free Threatpost webinar, AI and Cybersecurity: Tools, Strategy and Advice, with senior editor Tara Seals and a panel of experts. Click here to register.