Google last week during its I/O event described security tweaks that are part of its upcoming Android O operating system, which is expected to be released later this year.
New features are Project Treble and a new permission standard around the feature called Instant App. Also to be introduced with Android O are important hardening of existing security features tied to core Android components such as System Alerts, device permissions and verified boot, said mobile security experts. Google also announced a makeover of its security platform it now calls Google Play Protect.
Google’s security focus with Android O are important and will go a long way toward improving security and privacy in the platform, said Andrew Blaich, security researcher at Lookout.
“In Android O there are going to be some big changes that will affect app developers directly and also that end-users and device manufacturers will benefit from by proxy,” Blaich said.
Despite years of work to bolster Android security, Google’s efforts have been stymied by the nagging problem of fragmentation. With Android O, Blaich said, Google addresses those loudest security critics.
Project Treble is Google’s most ambitious security addition to Android O. It changes how third-party hardware developers will write code for Android O. The goal is to streamline the often maligned Android patching process.
Project Treble separates the hardware-specific drivers and firmware used by companies such as Samsung or Qualcomm from the Android operating system. The implications will be significant when it comes Google’s ability roll out OS patches without having to wait for things such as chipset compatibility. Google said by creating this modular base for Android, it will be able to support updates moving forward on older hardware that OEM partners may no longer support.
“With Project Treble, we are putting the Android OS framework and vender-specific implementations into different processes that communicate with each other using a standard vendor interface. The vendor interface will be maintained from version to version which means the new Android OS framework will run with minimal changes on top of an older device,” said Xiaowen Xin, product manager at Google, during a session at Google I/O on Android security.
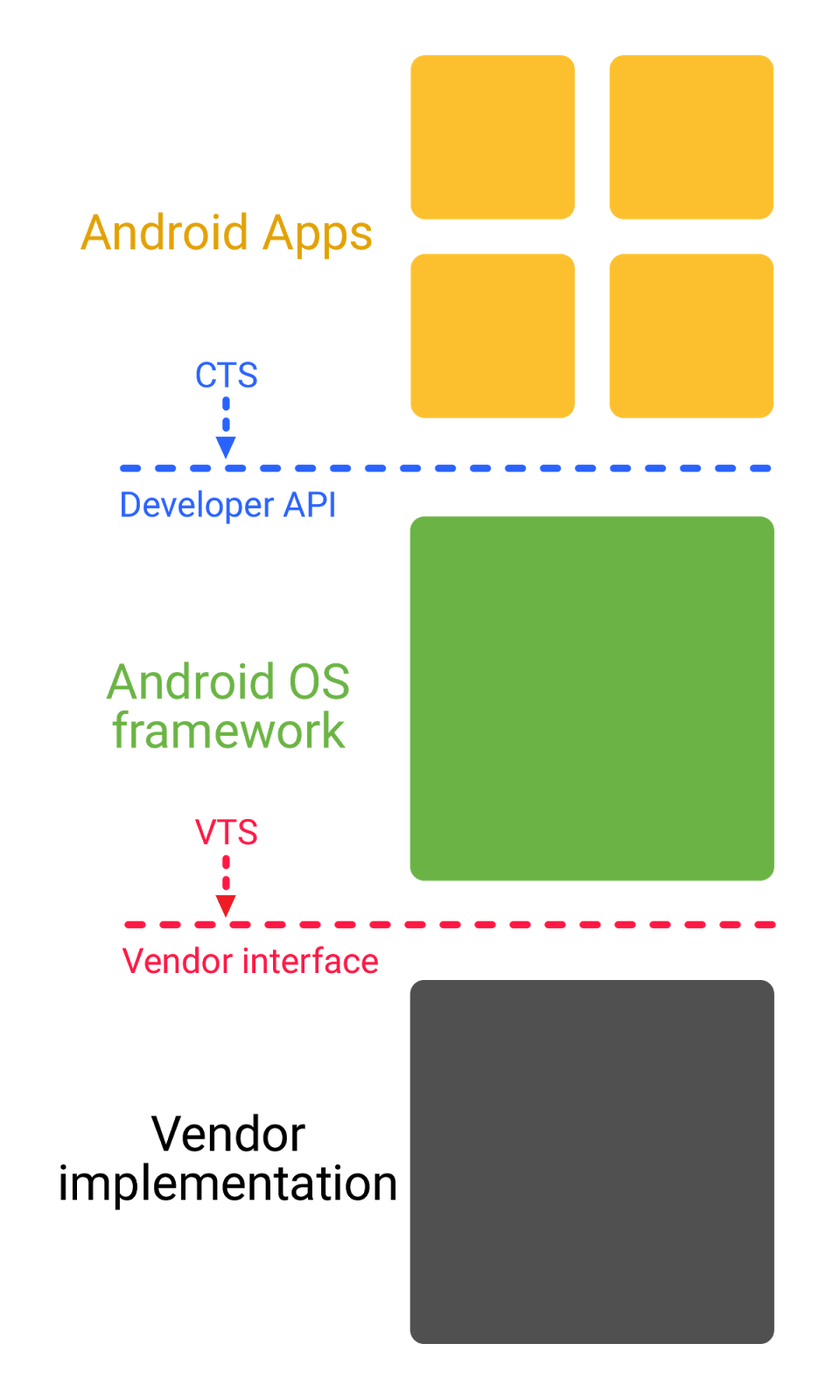 Xin explained that the modular approach to hardware and software, above, would also allow Google to limit aspects of the Android framework from accessing a device’s kernel.
Xin explained that the modular approach to hardware and software, above, would also allow Google to limit aspects of the Android framework from accessing a device’s kernel.
“So now we can put the Android framework pieces into tighter sandboxes, reducing the attack surface and making it harder to exploit vulnerabilities against the kernel,” Xin said.
Instant App is a feature introduced last year, but only recently opened up to all developers. Instant App, according to Google, allows Android users to run a developer’s app instantly, without installation. Instant App allows a app makers to create light or mini applications that can integrate with Android launcher. Apps can be initially run just by clicking on a URL and can be saved to the Android home screen. Part of the Instant App runs locally and another portion in the cloud.
“Instant Apps have a potential to greatly improve user experience as well as increase an apps user engagement and conversion numbers. On the other hand, opening up arbitrary URLs with Instant Apps also comes with associated security and privacy risks,” Xin said.
To reduce risk, Google is unveiling an updated permissions model for Android O. For example Instant Apps take a stronger stance on privacy (requiring HTTPS), removed access to persistent device identifiers and will limit permissions to sensitive OS components such as Contacts.
As part of Android O, Google said it will also beef-up security on its System Alert window functionality. The System Alert feature allows developers to create apps that can pop-up or display windows on top of all other Android apps running on a handset. This feature has been abused by malicious developers who create what users think are a persistent window on their Android device. Victims are asked to pay a ransom to make the window go away. In Android O, System Alert overlays will include visual notifications that can be clicked on to remove the overlay, Xin said.
“The fix proposed by Google should solve the current problem,” said Daniel Padon, mobile threat researcher with Check Point Software Technologies. “However, due to Android’s extremely low patch rate, most users will stay vulnerable to this type of attacks. Moreover, we have little doubt that malware writers will be able to find new ways to achieve their malicious goals.”
Check Point originally found and reported the System Alert flaw to Google two weeks ago.
Google will also expand its use of verified boot that will now prevent users from booting to older more vulnerable versions of the OS. It will also add support in the OS for EMV-like chips found in credit cards. Chip support will allow OEMs to build in user PIN authentication functionality for the device and services.
Android O is expected to formally debut in the third quarter; an alpha version was released in March.
“It will definitely take some time for the transition to Android O to occur, as evident by past adoption of newer Android versions, but over time the ecosystem will update and be more secure for it,” Blaich said.










