TheMoon, an IoT botnet targeting home routers and modems, is entering a new phase, as it were: It has added a previously undocumented module that allows it to be sold as-a-service to other malicious actors.
This has already had significant real-world consequences, according to CenturyLink Threat Research Labs, with the detection of a video ad fraud operator using TheMoon on a single server to impact 19,000 unique URLs on 2,700 unique domains over a six-hour period. It has also been seen being used for credential brute-forcing, general traffic obfuscation and more.
TheMoon is a modular botnet active since 2014, which targets vulnerabilities in residential routers within broadband networks. According to researchers, it exploits target broadband modems or routers developed by companies such as Linksys, ASUS, MikroTik and D-Link, with the most recent exploit added last May targeting GPON routers. It spreads like a worm, and has been seen incorporating as many as six IoT exploits at a time in an effort to increase its footprint.
The researchers said that the new module is only deployed on MIPS devices, a common microprocessor architecture typically found in residential gateways and modems. It allows the compromised device to be used as a SOCKS5 proxy. This means that it can be used maliciously to circumnavigate internet filtering or obscure the source of internet traffic, allowing the botnet author to sell its proxy network as a service to others.
“TheMoon is a stark reminder that the threat from IoT botnets continues to evolve,” said Mike Benjamin, head of CenturyLink Threat Research Labs. “Not only does TheMoon demonstrate the ability to distribute malicious modules of differing functionality, but it’s designed to function like a botnet-as-a-service, enabling other malicious actors to use it for [their own] uses.”
Netlab 360 has previously documented various TheMoon modules that can act as traffic proxies at the behest of a command-and-control (C2) server.
“Traffic flowing through the proxy network is roughly divided into plaintext and ciphertext, and the traffic is not high,” Netlab360 analysts said in a recent overview of TheMoon. “In the plain text, it is related to pornography, gambling, mining, etc., and a small part looks like a portal site; the traffic in the ciphertext section is related to e-commerce or online mailboxes. The time distribution is not obvious, it seems that traffic occurs 24 hours.”
This new iteration is different, according to CenturyLink. “Previous modules with proxy functionality only allowed the C2 to send proxy requests; the new module allows the botnet author to sell its proxy network as-a-service to others,” CenturyLink analysts said in a Thursday posting on the botnet. “The proxy port appears to be a randomly chosen port above 10,000 and was observed changing multiple times per day. Originally this proxy port was unauthenticated, allowing anyone to route traffic through an infected device. In April 2018, the actors changed their proxies to use authentication.”
In the video ad fraud example, CenturyLink analysts saw a quickly swelling attack.
“What we saw during this particular six-hour period was one operator leveraging TheMoon to conduct video ad fraud, essentially making it appear that thousands of people were clicking on video ads,” Benjamin told Threatpost. “Specifically, the operator used a single server to impact 19,000 unique URLs on 2,700 unique domains in that short time.”
CenturyLink, as a communications provider, blocked TheMoon infrastructure on its ISP network, in addition to notifying other network owners of potentially infected devices, so the activity of TheMoon dropped off as a result. 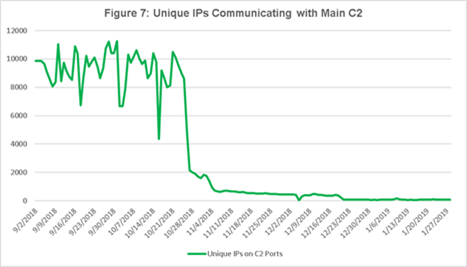
“That said, the threat of IoT botnets with varying capabilities remains a powerful one,” Benjamin noted. “It’s likely this actor will attempt to infect new devices in the future by adding additional exploits to the existing toolkit.”
The CenturyLink analysis also points out that there’s a substantial market for proxy botnets targeting broadband networks to route traffic for attacks like credential brute-forcing and ad fraud.
“The always-on nature of IoT devices and the ability to masquerade as normal home users make broadband networks prime targets for these types of attacks,” according to the firm.










