The traditional image of a successful email attack is that of a naive employee clicking the link in a crudely crafted spam email bent on phishing. But times have changed, and employees are much more security-educated than they used to be. So, today’s threat actors are creating increasingly sophisticated business email compromise (BEC) attacks that rely on social engineering and lack the common threat signals to trigger detection.
Email has been the leading attack vector for cyberattacks for years. Organizations have responded by investing heavily in email security solutions to combat everything from commodity spam and credential phishing, to ransomware in attachments.
BEC attacks are different because they do not have attachments carrying malware, nor do they contain URLs leading to malicious websites. The content of the email is generally simple, and the attacks are customized for each individual target.
As a result, BEC losses continue to grow, in spite of employees’ email-security awareness. According to the FBI’s Internet Crime Complaint Center (IC3), BEC scams have led to $26 billion in losses in the last three years.
BEC attacks in general represent a small portion of the total email attack pie. The Abnormal Security Research Team finds that of all the attacks our customers are facing, only 5 percent are BEC scams, which we refer to as “payload-less.”
However, while this is a small percentage compared to payload-based spam and malware campaigns, BEC attacks are nearly always hand-crafted and incorporate heavy elements of social engineering. As such, they disproportionately represent the greatest financial risk. And to boot, the payload-less nature of these BEC attacks evades detection from traditional email security solutions.
Through investigations within its Threat Center, the team has uncovered the most common characteristics of payload-less attacks and statistics related to how often they are used by threat actors. Before the pandemic, in February, the team observed that the most common characteristics included:
- 65 percent of BEC emails: Engagement (the threat actor asks something like “Can you assist with two payments before noon?”)
- 18 percent: Bitcoin Extortion
- 10 percent: Gift Card Fraud
- 7 percent: Fraudulent Payroll Update
Unsurprisingly, over the past few weeks the Abnormal Security Research Team has observed that the majority of email attacks have a COVID-19 related element. In April, the team saw a 90 percent increase in coronavirus-related attacks. It found that the majority of attacks were driven by COVID-19 spam, which had increased by 150 percent. Attacks have included COVID-19 vaccine donation scams, WHO donation scams, COVID-19 medication scams, stimulus payment attacks and Zoom malware attacks preying on job-layoff fears.
BEC Example Emails
Executive Impersonation: Executive Impersonation is a common example of BEC and one of the easiest for attackers to execute. These attacks are very challenging to detect due their simplicity and, frankly, their elegance. Emails may be coming from reliable and known email services such as Gmail. Due to their widespread use, emails from those sending domains cannot be simply blocked.
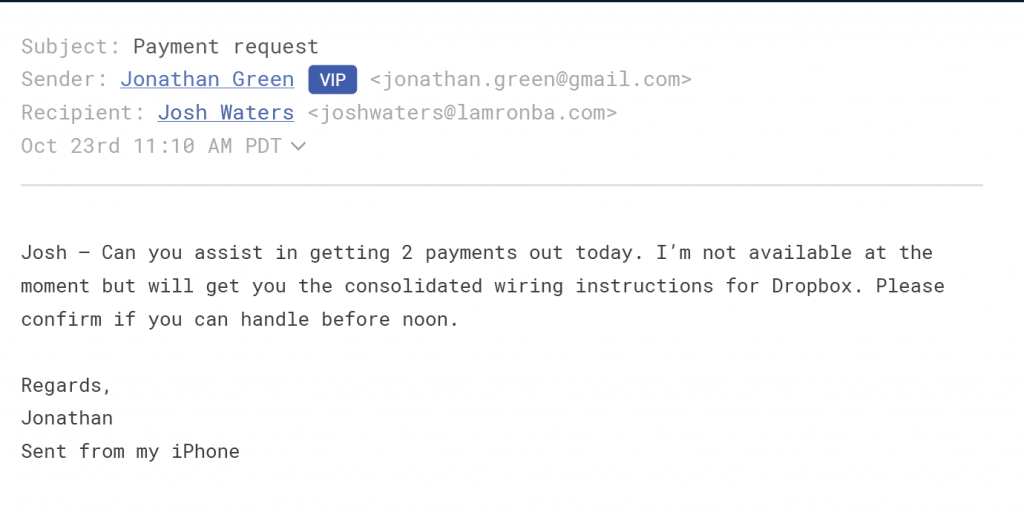
Vendor Compromise/Conversation Hacking: Compromised vendor accounts are an extremely difficult attack to identify. The emails are coming from trusted relationships and attackers may reply back to an existing email thread to further seem credible.
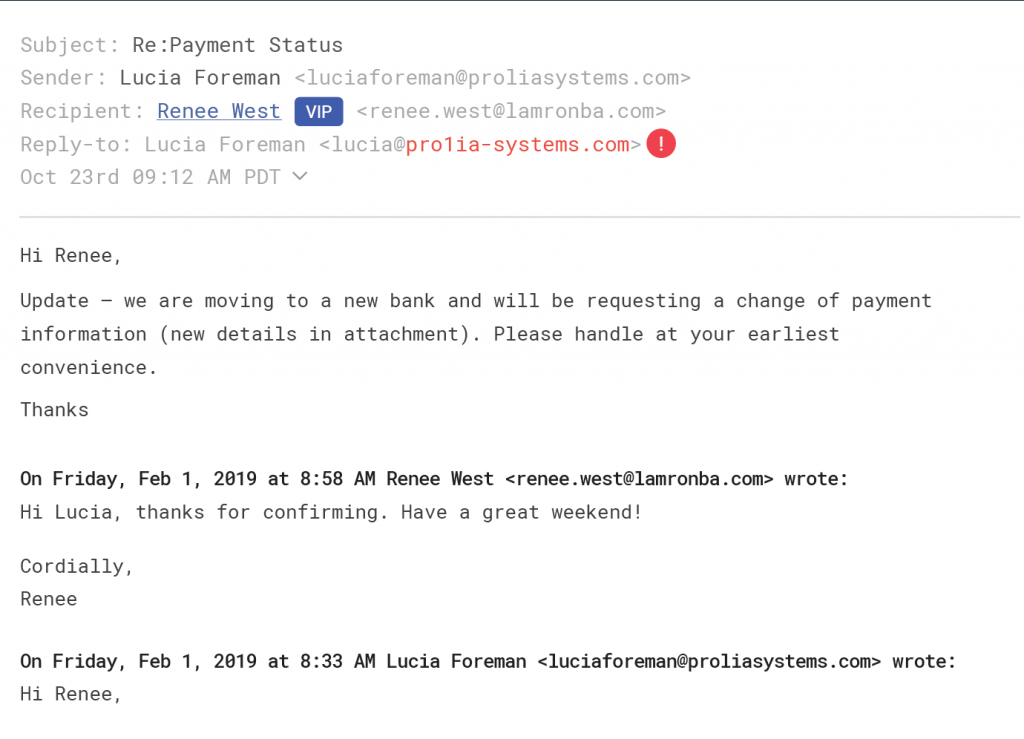
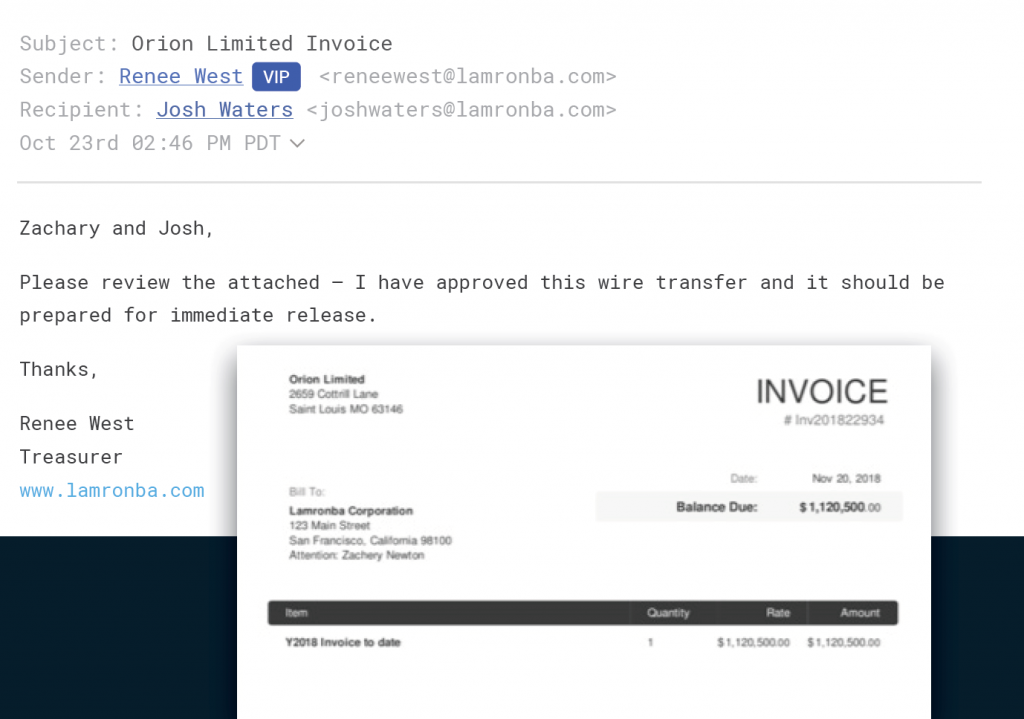
Employee Compromise: Similar to compromised vendor accounts, attacks from internally compromised accounts are also extremely difficult to identify. Not only are the emails coming from trusted employees, the internal-to-internal (i.e., intra-domain mail flow) is not commonly scanned by traditional email security solutions.
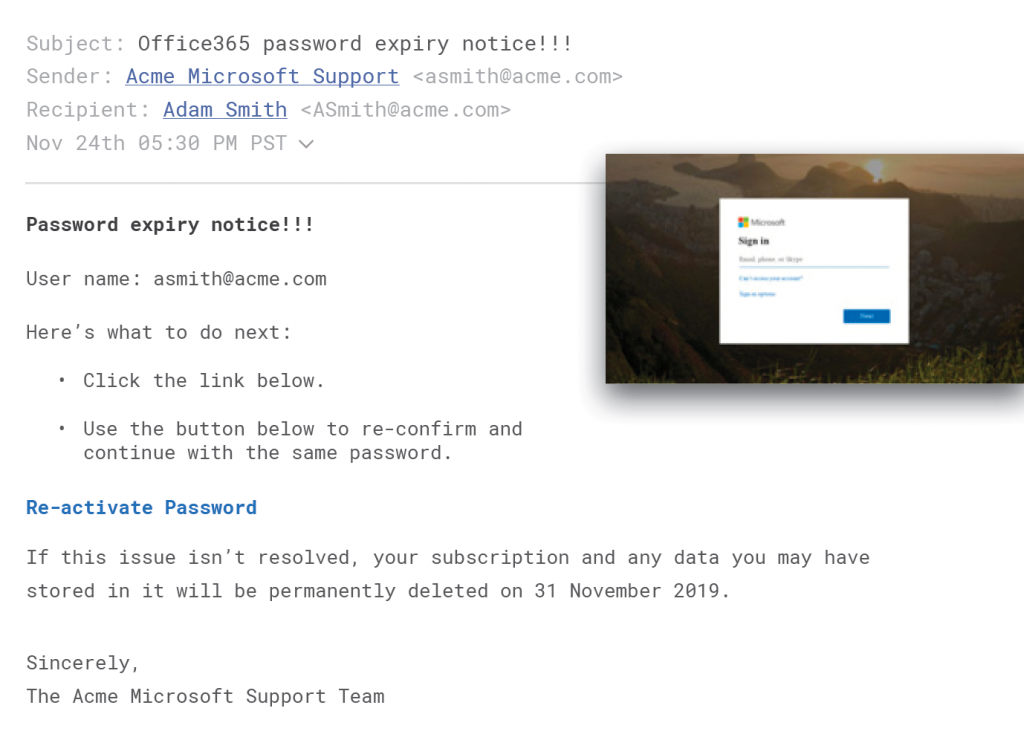
Credential Phishing: Most credential phishing attempts are impersonation attempts of a known brand such as Microsoft, Amazon, FedEx, Google, etc. While some email security solutions may detect these attacks (high entropy URLs, previously seen URLs as part of a threat intelligence source, etc.) these attacks are difficult to reliably catch. Also, the credential-phishing sites do not typically contain malware, making typical sandboxing approaches ineffective.
How to Protect Against Modern Social-Engineering Attacks
According to the Abnormal Security Research Team, 69 percent of payload-less attacks impersonate someone the recipient knows; while employees are 17 times more likely to engage with a payload-less attack email than they are with with other types of phishing and spam.
In order to protect against modern social engineering attacks, today’s security teams need to analyze a broader set of data in order to better understand the context of communications. For example:
- Perform identity modeling of both internal and external (partners, vendors, customers) entities, and analyze more data sources as a part of that modeling.
- Create relationship graphs to understand not only the strength of each connection and the frequency of communication, but also the content and tone of the communication.
- Perform email content analysis using techniques like computer vision techniques, natural language processing, deep URL analysis and threat intelligence.
These techniques will provide automated insights that a human analyst can review. The increasing sophistication of attacks means that security teams need to employ more sophisticated protections. Leveraging techniques that offer a better understanding of the context of communications is the best place to start.
Evan Reiser is the CEO and co-founder of Abnormal Security. He most recently led product and machine learning teams at Twitter after co-founding successful companies including Bloomspot (acquired by JPM Chase) and AdStack (acquired by TellApart).
Enjoy additional insights from Threatpost’s InfoSec Insider community by visiting our microsite.










