As 2020 draws to a close, it’s clear that work-from-home security, ransomware, COVID-19-themed social engineering and attacks by nation-states will go down as defining topics for the cybersecurity world for the year. Threatpost also took a retrospective view on what readers were most interested during the last 12 months, looking at our top five most-read stories of the year.
Please read on to learn more about what caught reader’s attention the most this year, with an eye to summing up some hot trends. Subjects include Microsoft Office 365; major security bugs in Zoom and other platforms; gaming security; the ongoing scourge of Emotet and malware development in general; and concluding with a potpourri of other hot 2020 headlines involving WhatsApp, code-cracking and more — along with our top multimedia stories.
1. Microsoft: Office 365 and More
With enterprises relying heavily on Microsoft’s business suite of applications during the COVID-19 pandemic, cybercriminals supercharged their targeting of these tools across a variety of attack vectors.
Most-Read Story of 2020: Microsoft Teams Lure
One cybersecurity story caught more reader interest than any other article for the year: Phishes that pretended to be automated messages from Microsoft Teams. The attack, uncovered in October, was sent to between 15,000 to 50,000 Office 365 users, in hopes of scooping up their credentials.
Teams is Microsoft’s popular collaboration tool, which has particularly risen in popularity among remote workforces during the pandemic – making it an attractive brand for attackers to impersonate.
“Because Microsoft Teams is an instant-messaging service, recipients of this notification might be more apt to click on it so that they can respond quickly to whatever message they think they may have missed based on the notification,” said researchers at the time.
Microsoft Office 365: Top Threat Vector
Many of this year’s top-level phishing attacks leveraged Microsoft-themed lures in order to steal Office 365 credentials. For instance, one spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets. Attackers also shook up their phishing tactics, with one September phishing campaign using authentication APIs to validate victims’ Office 365 credentials – in real time – as they entered them into the landing page, for example.
Microsoft 365 Bugs
Flaws were found in Microsoft’s lineup itself as well, with issues in the multi-factor authentication system used by Microsoft’s cloud-based office productivity platform, Microsoft 365, opening the door for hackers to access cloud applications via a bypass of the security system.
2. Bug Parade 2020
In 2020, there was a 65 percent increase in the discovery of high-risk vulnerabilities, according a year-capping Bugcrowd study. Few companies knew this stat better than overnight-sensation Zoom, who found itself on the receiving end of a number of critical bug notifications.
Topping our list of Zoom’s 2020 bugs, and driving serious interest with Threatpost readers, were two zero-day flaws found in the macOS version of the Zoom client and disclosed on April Fool’s Day. The flaws, uncovered by Patrick Wardle, principle security researcher with Jamf, allowed a local and unprivileged attacker to gain root privileges of a targeted system and gave them access to the victims’ microphone and camera.
Cisco Systems: A Top CVE Squasher!
When you are one of the world’s leading information technology and networking companies, you’re going to have some bugs. In 2020, Cisco Systems deserves props for its transparency and efficiency when it comes to notifying customers and patching hundreds of vulnerabilities. Let us reminisce. In early December there was the zero-click wormable RCE vulnerability in Cisco Jabber that was patched – twice. From zero-clicks to zero-days, Threatpost readers turned their attention to a nasty, at the time, unpatched AnyConnect Secure Mobility Client Software bug. After the bug was patched, Cisco confirmed said there were no reports of attacks against the flaw before it was fixed.
3. Gaming Security
Gaming security came more into focus for readers in 2020, as a possible result of the global COVID-19 pandemic. Thanks to a long few months spent with reduced social outlets, gaming audiences have exploded this year. That’s attracted the attention of cybercriminals – in a recent survey by Kaspersky, nearly 61 percent reported suffering foul play such as ID theft, scams or the hack of in-game valuables.
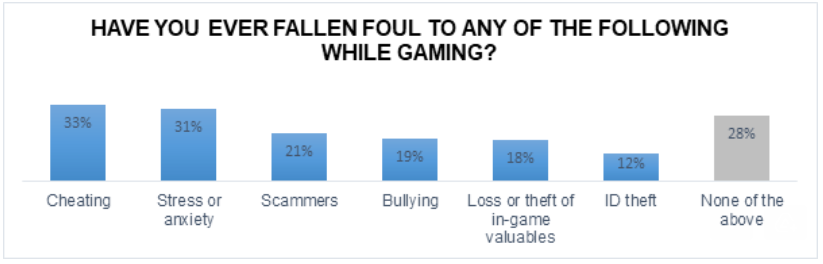
Source: Kaspersky.
Among Us Mobile Game Crashes
One of Threatpost’s Top 5 most-read stories covered the meteoric rise of the game Among Us, and how it outpaced its developer’s ability to keep up with malicious actors.

In October, a specific ongoing attack forced InnerSloth, the company behind the game, to hastily roll out an update designed to kick bad actors off the game’s servers — likely along with some innocent players as well. InnerSloth is run by a three-person team consisting of one developer, one animator and game designer, and one artist.
The attacks spammed players with ads from a player named Eris Loris, rendering the game useless. The attackers used bots to overwhelm the game with messages promoting a YouTube channel and Discord operated under the name Eris Loris, threatening to “blow up your phone,” and concluding with a “Trump 2020” endorsement.
Cyberpunk 2077: Gaming Event of the Year
Gaming security news in general was in-demand in 2020. The December release of Cyberpunk 2077, featuring a digitized Keanu Reeves among other things, was supposed to be the gaming event of the year. Instead, the initial release was slammed for poor performance and numerous bugs and glitches that make the user experience less than pleasant – forcing Sony to pull the game off the PlayStation store.
On top of that, cybercriminals waded into the mix, spreading ransomware targeting Android devices disguised as a legitimate download of the new open-world game.
The CoderWare ransomware was being promoted as a download of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace. The listing for the game, which is named “Cyberpunk 2077 Mobile (Beta),” even had reviews from users so as to appear legitimate.
NVIDIA Bugs: Fuel to the Fire
Cybercriminals didn’t just target the games themselves in 2020; they also went after bugs in the systems that gamers rely on. Nvidia, which makes gaming-friendly graphics processing units (GPUs), was a particular hot target throughout the year,
In October it disclosed two high-severity flaws in the Windows version of its GeForce Experience software. GeForce Experience is a supplemental application to the GeForce GTX graphics card — it keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure.
In June, Nvidia fixed two high-severity flaws that affected drivers for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. And in March, Nvidia issued patches for high-severity bugs in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks, and also affected display drivers used in GeForce (as well as Quadro and Tesla-branded) GPUs for Windows.
Scalper-Bots Ruin Christmas
Another popular gaming headline this year involved another hotly anticipated release in the gaming world: New consoles from Microsoft and Sony: The Xbox Series X and PlayStation PS5, respectively. But an army of bots threatened to drive prices up as much as three times the retail price, putting the coveted holiday gifts well out of reach of everyday fans.
Retailers were quickly cleared out of Xbox inventory on its release day. There were plenty available on eBay though, with price tags more than double that price, several marked at over $1,000. The PlayStation 5, also priced at $499.99, experienced several pre-order confirmations — not even actual product — available on eBay listed for around $900.
The activity sparked the development of the “Stopping Grinch Bots Act,” introduced in the Senate in December, which would ban bots on all online retail platforms if passed.
4. Malware Mayhem
In our fourth hot-topic area, malware authors throughout the year found new ways to snoop on victims, steal sensitive data and more by creating new strains of malware, and improving on older ones.
One of these strains was a self-propagating malware, found in June, called Lucifer. This malware targeted Windows systems with cryptojacking and distributed denial-of-service (DDoS) attacks.
In addition, cybercriminals made critical updates or adopted new attack techniques as part of existing, well-known malware families. For instance, in November attackers sent out ads for fake Microsoft Teams updates to deploy backdoors, which used Cobalt Strike to infect companies’ networks with malicious code.
Emotet’s Evolution Continues
Emotet, which started as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism, continued its track on 2020 to become a top threat. One of Threatpost’s Top 5 headlines of the year came in February, when a new Emotet malware sample was uncovered with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device. Also in February, researchers warned of an Emotet campaign being spread via SMS messages. The messages pretended to be from banks, and researchers warned the campaign may have ties to the TrickBot trojan.
Emotet continued to be a thorn in defenders’ side over the course of 2020, picking up a series of new tricks. First, Emotet’s attachments started to include password-protected archive files to bypass email security gateways. Soon after, Palo Alto Networks reported to CISA that researchers are now seeing instances of “thread jacking” — that is, intercepting an existing email chain via an infected host and simply replying with an attachment to deliver the malware to an unsuspecting recipient.
And the threat isn’t limited to desktop computers. Steve Banda, senior manager of security solutions at Lookout, told Threatpost Emotet has gone mobile this year, too.
The activity led the Feds this fall to issue a warning that state and local governments need to fortify their systems against the trojan.
Mobile Malware Attacks Surge
Attackers honed in on mobile as a target for their malware campaigns this past year, too. The Joker malware (a billing fraud family of malware that emerged in 2017) continued to rock the Android ecosystem, with Google in January announcing it had removed more than 17,000 Android apps from its Google Play marketplace. In a separate July report, researchers said that 14.8 percent of Android users who were targeted with mobile malware or adware last year were left with undeletable files. It’s not just mobile – browsers were also a top vector for spreading malware in 2020, with researchers finding 500 Google Chrome browser extensions in February secretly uploading private browsing data to attacker-controlled servers, and redirecting victims to malware-laced websites.
5. The Best of the Rest
Positive Encryption News
Whether it be browser support for HTTPS or safer certificate deployment, positive developments around encryption technology attracted considerable interest with readers. In March, internet behemoths like Google took an even harder stance against the insecure Hypertext Transfer Protocol (HTTP) and began warning Chrome browser users when the downloads from sites lacked the more secure Hypertext Transfer Protocol Secure (HTTPS) protection. Later in the year, browser makers adopted DNS-Over-HTTPS (DoH) support – both a privacy-boosting and security enhancement.
2020 Social Media News Wrap
Social platforms such as Facebook, TikTok and WhatsApp also dominated Threatpost virtual foot traffic. A well-worn path to WhatsApp news stories included headlines “WhatsApp Phone Numbers Pop Up in Google Search Results” and “WhatsApp Bug Allows Malicious Code-Injection“. TikTok being banned by the United States Army drew interest in January 2020 setting the tone for stories to come such as TikTok owner ByteDance’s security posture around the app and the possible sale or ban of TikTok from U.S. markets altogether. As for Facebook, readers were hungry for news in November about how a Facebook Messenger bug that allowed spying on Android users. Facebook’s Messenger client also piqued reader interest in May with a report about Android malware, dubbed WolfRAT, that was being deployed to gather intelligence on victims.
Media Beat: Podcasts, Webinars and Video
When COVID-19 cut Threatpost’s ability to travel to conferences and interview important voices in the security community one-on-one and in person, we adapted. Senior Editor Lindsey O’Donnell Welch produced an impressive library of videos and podcasts in 2020.
As for videos, one of our most popular segments featured Chris Vickery, the director of risk research with UpGuard who discussed how artificial intelligence will drive next-gen breaches. She also caught up with Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, who discussed cyber vigilantes.
Podcasts our readers enjoyed the most included “Malware Risks Triple on WFH Networks: Experts Offer Advice“. The second-runner up podcast featured Ryan Olson, vice president of Threat Intelligence for Unit 42 at Palo Alto Networks, and May Wang, senior distinguished engineer at Palo Alto Networks and former Zingbox CTO, who each weighed-in on IoT devices vulnerabilities.
Top Threatpost webinars included “Taming the Unmanaged and IoT Device Tsunami” which featured cybersecurity expert Bruce Schneier and Armis CISO Curtis Simpson. A second webinar on healthcare security titled “2020 Healthcare Cybersecurity Priorities: Data Security, Ransomware and Patching” featuring Jeff Horne, CSO at Ordr and Tony Reina, chief AI architect at Intel, was our second most popular — it was entitled “More Than Half of IoT Devices Vulnerable to Severe Attacks.“













